
By understanding the illegal goods and services offered, the consequences and dangers involved, and the challenges faced by law enforcement, you can better protect yourself and your organization. Money laundering and financial crimes are major concerns in the context of navigating the threat landscape, with darknet markets playing a significant role. As an individual seeking belonging, it’s crucial to understand how money laundering techniques and regulatory frameworks impact our society. With these options at your disposal, you can find a sense of belonging within the world of darknet markets.
The users on this site can review and rate the products that promote reliable and fraudster vendors. Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum. These digital currencies provide a degree of anonymity, as transactions are recorded on a public ledger but do not directly link users to their real-world identities. To purchase illicit goods or services, users deposit cryptocurrency into an escrow system or directly to the seller, and the cryptocurrency is held until the buyer confirms the satisfaction of the transaction. The market started in 2021 in Canada and features both international and Canadian users.
- This makes it more difficult for authorities to locate and take down these sites.
- For example, China uses the Great Firewall to block access to Western sites.
- The email service is available both on the surface and on the dark web.
- With global efforts and initiatives in place, we can combat these dark corners of the internet and ensure a safer society for all.
- This is where cybercriminals go to buy and sell things like stolen credit card numbers, personally identifiable information (PII), and even SSH login details.
Indicators Of Compromise In Threat Intelligence
While there are several darknet markets, each features unique characteristics tailored to various user needs. Discover everything about what is a darknet market, how it works, security threats related to it, and learn how to protect your data online. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation.
How To Access onion Sites Safely
Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. Monero and Bitcoin are two of the most commonly used digital currencies on the dark web markets. Due to being the most popular and the oldest coin, Bitcoin is traceable. However, Monero, on the other hand, is untraceable and the most trusted payment method on these markets.
Its focus on financial fraud and high-value transactions has attracted a dedicated user base, contributing to its growing reputation and market value. To expand their reach, some marketplaces established parallel channels on Telegram. This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself. Chainalysis data shows darknet marketplace revenue dropped post-Hydra seizure in 2022 but recovered to $2 billion in Bitcoin inflows during 2024 Darknet market BTC inflow drop and shift to Monero. Abacus alone represented nearly 5 per cent of total DNM revenue, underscoring the ongoing scale of underground commerce. Archetyp Market was dismantled in June 2025 during Operation Deep Sentinel in a coordinated raid across six countries.
Russian Market
Eventually, the system collapses, and most people lose their entire investment. Drug dealers can sell to customers across the world, not just locally. This expanded reach, combined with anonymity, only makes it easier for them to grow their operations without getting caught immediately.
Overview Of Darknet Markets
Perhaps, the lack of rules and anonymity of the dark web can be tempting, but those are the same things that make it a risky environment. Moreover, it’s not only the entertainment industry that gets hit; some sell cracked versions of the most expensive software, and others offer pirated eBooks and academic material at cheap prices. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. If you ever decide to explore the dark web, protecting your identity is crucial.
A Massive Mobile Location Data Hack May Have Risked Gay People’s Safety
Since these providers may collect personal data like your IP address we allow you to block them here. Please be aware that this might heavily reduce the functionality and appearance of our site. Additionally, where non-compliant cash out points are facilitating the movement of illicit funds from DNMs, regulators and law enforcement may take action to disrupt activity at the cash out point itself.

Experience The World’s Most Advanced Cybersecurity Platform

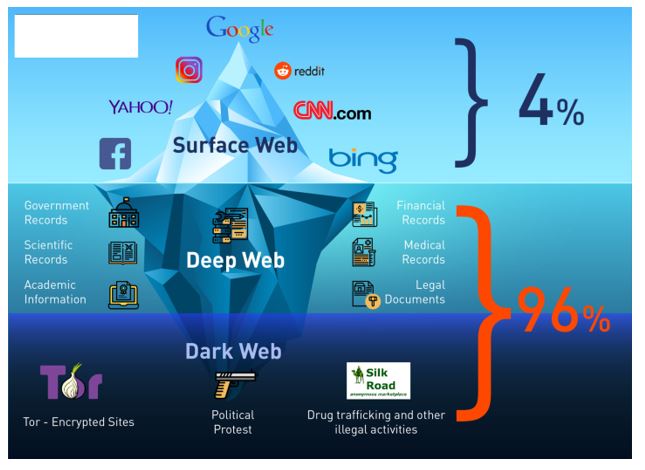
In Ohio, officers arrested several members of a group called Pill Cosby, who had allegedly mailed more than a million pills laced with fentanyl. The Department of Justice noted that DisrupTor was initiated after “U.S. Claire Georges, a spokeswoman for Europol, confirmed to me recently that DisrupTor was “entirely designed around” that first cache of information from CyberBunker’s servers. There are a lot of misconceptions about the dark web online and in popular media. When most people refer to the dark web, they are thinking about dark web/darknet marketplaces (DNMs).
The most important thing is to ensure that you never click on links that you’re not sure of their source. Also, it should be common knowledge not to share personal information online. In this era, it takes one wrong click and all your sensitive data ends up in the wrong hands. Therefore, you need to take your privacy seriously and start by using strong and unique passwords for every online account you open. The dark web is not a place that you can venture into without protection and caution; a slight slip-up can lead to major consequences.
The CSO Guide To Top Security Conferences
Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience. This site supports PGP encryption and two-factor authentication features. Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce.
Operations
The site allows users to find and buy a vast variety of products and services. It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. Established in 2020, Awazon Market has quickly become one of the most famous darknet marketplaces. You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection.
Srinivasan received virtual currency as payment for the drugs and then routed that virtual currency through cryptocurrency exchanges. On Dec. 16, 2024, Rui-Siang Lin pleaded guilty to charges brought by the U.S. While the dark web is not illegal, mainstream awareness of the darknet is tied to the rise of the Silk Road, an online black market founded in 2011 by Ross Ulbricht. The Silk Road was especially known for its role in the online drug trade but was host to other illegal transactions until it was shut down by the Federal Bureau of Investigation in 2013. These listings often include detailed descriptions, user reviews, and even shipping guarantees. Malicious vendors often infect buyers with spyware, ransomware, or infostealer malware hidden in downloadable files.



