There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely. The second category consists of data stores, which specialize in stolen information. This shadow economy supports a full-fledged cybercrime supply chain, from data theft to monetization, further complicating mitigation efforts. A single campaign may test thousands of cards within minutes, overwhelming servers and bypassing simple rate-limiting tools. mark it means it has been verified as a scam service and it should be avoided. This gives security teams time to adjust their defenses before new techniques become widespread.|Stolen credit card details can be categorized into different types, making it easier for cybercriminals to exploit them. Dark Web credit cards can be a nightmare for victims, often leaving them with significant financial losses and damaged credit scores. Some of these restaurants had no clue they were hacked until the Secret Service came to their door. When Target was hacked in 2013, customer card details turned up on dark web marketplaces.|Corporations and governing bodies alike currently participate in unauthorized surveillance of online activity. Explore a diverse selection of goods and services, with a focus on privacy and security. Despite its darker reputation, the dark web also provides a platform for individuals who are concerned about privacy or who seek to discuss sensitive topics without the risk of government surveillance. Two terms often mentioned when discussing these hidden areas are the deep web and dark web.|I recommend enabling automatic updates and checking for new versions before each session. Our platform alerts security teams when an organization’s sensitive data is found. The intelligence gathered from these markets helps security teams predict and prevent future attacks. Monitoring these sites also helps track the effectiveness of security investments. When used correctly, it provides strategic intelligence that can prevent major financial losses. These generated numbers link to your real card but can be limited by merchant, amount, or time.}
Market Value And Popularity
- The price for cloned cards varies depending on the credit limit, with an average price of $171.
- Posting or replying to someone’s post does require registration which is free, instant and anonymous.
- However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it.
- Notice how it normalizes fake data buying by including buyer ratings and comments.
- The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption.
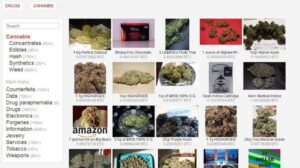
Educate individuals and businesses about the risks of carding and how to identify and avoid potential threats. While some of these markets were shuttered by law enforcement agencies – some took the easy way out with exit scams. Here are some of the now-defunct dark web markets that were notorious for cybercrime. Launched in September 2022, Torzon Market operates on the Tor network and features over 11,600 illegal products, including drugs and hacking tools. It enhances buyer transparency by importing vendor feedback with PGP proof.
One option is to try DuckDuckGo’s .onion version, which is great for privacy. Other options include Ahmia and NotEvil, which focus on listing .onion links. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies.
- Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions.
- The BBC Tor Mirror is an international version of the BBC that focuses on world affairs, and it’s extremely useful for those who live under strict censorship laws.
- A free Dark Web scanner like the one offered by Identity Guard can provide this information quickly and easily — but it won’t show you all of the information to which hackers have access.
- Scammers use this data for malicious activities like identity theft and account takeover.
- Facebook’s dark web version allows users to access the site where it is banned or restricted.
- Some even say that the real dark web requires an invitation to participate.
In addition to new scams and schemes targeting online banking customers, we have seen the evolution of criminal marketplaces to trade in stolen information, stolen accounts, and stolen money. This has been a particularly interesting history of development around stolen payment card information. Spoofed websites are sites that have been made to look legitimate but are actually designed to steal your sensitive information. Depending on the goal of a cybercriminal, they may prompt you to enter your login credentials or your credit card information. NordVPN analyzed statistical data gathered by independent researchers specializing in cybersecurity incident research from markets where payment card numbers are being sold.
It is a relatively new provider but offers better features than most established VPNs. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. Most likely, the native account on your device has full admin permissions by default. Therefore, you can prevent this exploitation by setting up a non-admin account. Also, use an effective antivirus program to check threats if you decide to download files.
Local Law Enforcement
These platforms leverage advanced encryption technologies and decentralized systems to ensure secure transactions and protect user identities. Below is an analysis of the top verified darknet marketplaces that have gained prominence for their efficiency and trustworthiness. In 2025, the landscape of darknet markets has evolved significantly, offering users enhanced security, reliability, and a streamlined experience for drug trade.
Popular Carding Techniques
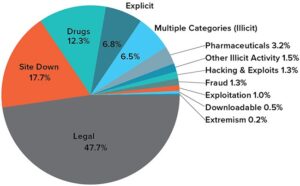
Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025. We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. It’s important to stay vigilant as you browse online, interact with other users, and share your credentials on numerous platforms. For example, two months ago a Russian national was arrested in Arizona for allegedly deployed LockBit, Babuk, and Hive ransomware. The increased law enforcement activities of the past year are changing the landscape of cybercrime—one of the dark web trends about which we can all be happy.
How Can You Access Darknet Carding Sites?
Sellers, on the other hand, face the risk of being caught and prosecuted by law enforcement agencies. Additionally, darknet carding sites are often targeted by hackers and cybercriminals, who may attempt to steal the credit card information being sold or otherwise disrupt the site’s operations. Darknet carding sites typically operate using a marketplace model, where users can buy and sell credit card information. The sites are often accessible only through the Tor network, which provides anonymity for users.
No one truly knows the size of the dark web, but some estimate that it accounts for just 5% of the total internet. For an added layer of protection, consider purchasing a virtual private network, or VPN. A VPN provides you with anonymity by creating a private network from a public internet connection. Sites on the dark web don’t come with easy-to-remember URLs, and many disappear suddenly. The UAS Store – seized alongside Ferum, Trump Dumps and Sky-Fraud – was a popular seller of stolen remote desktop protocol (RDP) credentials.
WeTheNorth Market
Identity protection companies monitor information being sold on the dark web. If you’ve signed up for any sort of identity protection or credit monitoring service, you may get a notification that your credit card information was detected. For this reason, it’s far more important to be proactive about your online security. In the world of cybercrime, darknet carding sites have emerged as a significant threat to individuals and businesses alike.
Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki.
How To Delete Yahoo Account In 2025
Listen to Nethone’s Intelligence Specialist Michał Barbaś to learn more about fake carding forums and markets. Dark web websites look pretty much like any other site, but there are important differences. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t. No, darknet carding sites engage in illegal activities related to fraud and identity theft, making them highly illegal.
Dark Web Links: The Best Onion And Tor Sites In 2025
Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer. Currently, registrations are temporarily suspended due to an overload and lack of time (or so they say).
Can Authorities Track Transactions On These Sites?
Active since November 2017, UAS made around $3 million in cryptocurrency proceeds, of which $862,000 was made during the pandemic according to Elliptic’s internal data. The site also sold access to proxies, which allowed criminals to further anonymize their web usage. Adopt safe browsing habits, such as avoiding suspicious websites and downloads.

The Outseer Platform
Those who want to browse and use the Dark Web need to use specialized software, such as the Tor browser. Because it’s such a big part of internet activity, it’s worth noting how this Dark Web browser works and why it exists. The Deep Web hosts information that usually requires a username and a password to access, mainly for security and privacy-related reasons. Darknet carding sites are a significant concern for both individuals and businesses.