Malware and scams are scattered like landmines around the dark web. And with many unfamiliar-looking sites on the dark web, it’s harder to distinguish safe websites from shady ones, and easier to fall victim. To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing. Tor has an in-build slider which lets you adjust the level of security.
Meanwhile, cybersecurity experts monitor the dark web, scanning for stolen data and emerging threats. If your information surfaces in these murky depths, there’s very little you can do – but knowing the risks involved is a first step toward defence. From information security threats like identity theft and malware to scams and surveillance, navigating the dark web without caution can lead to real dangers. So, is the dark web a lawless underworld or a misunderstood frontier for privacy and free expression?

Myth 4: The Dark Web Is Inherently Dangerous To Visit
Also, you must log in or have a specific IP address or URL to access the deep web content. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy.
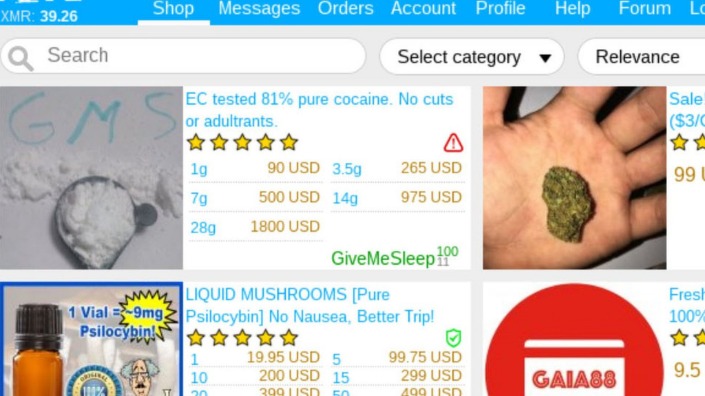
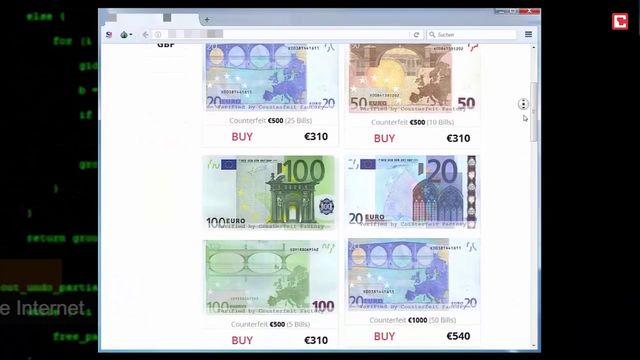
Topics And Products Sold
But privacy is fragile – using a VPN alongside Tor and maintaining strict security habits is crucial. The dark web is a section of the Internet not searchable through traditional search engines, where privacy and anonymity reign. It is notorious for illegal transactions and activities such as drug trafficking, arms dealing and identity fraud. It also provides a safe haven for whistleblowers, journalists and those seeking free expression under oppressive regimes.
How Do I Find onion Websites Safely?
You won’t find any “hidden” stories here—it’s the same content as the normal web edition—but users in countries with government censorship will appreciate having a secure way to access it. Whether your search engine of choice is Google, Bing, Baidu, Yahoo! The true internet – that which includes content not indexed by these search engines – is hundreds of times bigger.
These sites aren’t indexed by search engines like Google, so you can’t find them via traditional means. The websites and online platforms that you find via your search engine are actually only a small part of the internet. There are many more sites hidden away in a part of the internet called the deep web. Some of them (the hardest ones to access) are situated in what is known as the dark web. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
- Even completing a transaction is no guarantee that the goods will arrive.
- This makes it incredibly difficult to find out who you are paying.
- With your device running a Tor browser, you can go to Tor-specific sites – those with an .onion suffix — or also visit the usual sites on the open web.
- First things first, always use strong and different passwords for each account you open.
- You can sign up for the service completely anonymously, use a cryptographically signed installer, and double up on encryption using MultiHop servers.
To help find functioning .onion URLs, look to dark web directories and forums — Reddit users recommend tor.taxi, tor.watch, daunt.link, or one of the Hidden Wikis. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe.
Join Our Newsletter
The dark web exists to provide users with anonymity and privacy on the internet. Some users, such as whistleblowers or journalists working on sensitive issues in oppressive authoritarian governments, need privacy to carry out their activities. It’s incredibly common for darknet marketplaces to be held for ransom by hackers or attackers. These attacks usually involve DDOSing (overloading) the service and demanding a crypto payment from the site admins to stop the attack.
Is It Safe To Use?
Take a look at your Tor Browser settings before you start your first dark web browsing session. It has a range of settings you can configure to help with security and privacy. Disabling JavaScript, ActiveX, and Flash plugins, for example, will help to strengthen your privacy, though this may also cause some sites to run poorly. It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder.
These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft.
VPNs And Proxies: Practical Alternatives
- The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you.
- This includes using strong, unique passwords and regularly updating security software.
- Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+.
- Another vital precaution is to ensure that your .onion URLs are correct.
Other options include Ahmia and NotEvil, which focus on listing .onion links. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage.
Installing the Tor Browser is the best way to access the dark web. However, your online activity is encrypted and hidden from view thanks to Tor’s onion routing. This means your ISP can’t see that you’re accessing the dark web (or indeed, the specific sites you’re accessing). While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. The darknet is often considered a hidden part of the internet, where data and information are inaccessible to ordinary users.
Identifying specific individuals who use the dark web can be quite tricky. However, we advise connecting to one of our recommended VPN services to stay anonymous. The Tor network was created by the US military in the 1990s for anonymous communication between spies over the internet.
Cybersecurity Workforce Trends In 2025 – Skills Gap, Diversity And SOC Readiness
The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. The users of the dark web are typically aiming to block governments from snooping on them.