However, the protocol changes made by the currency users’ agreement. An extensive assortment of beneficence includes end users, nodes, miners, developers, and in-line industry contributors like wallet providers, exchanges, and custodians. Initially, there were only a restricted amount of new seller accounts accessible; new sellers had to obtain an account via an auction. Later, every new seller account was charged at least cost over 100,000 customers who used Silk Road to buy products and services. However, all transactions were conducted in cryptocurrency (Bitcoin), guaranteeing anonymity. While this search engine also demonstrates its index number of concealed URLs and includes the aptitude to chat with other users worldwide without any login or signup.
How Do I Find onion Links For Sites?
Thankfully, you don’t need to use your official name or email; just use a fake username (we tested it successfully). The site doesn’t require an email verification, though it offers all the features and security that you want in a dark web marketplace. To access onion sites, users need a stable internet connection and the Tor browser.
Best Dark Web Sites In 2025 + How To Stay Safe

The dark web is an encrypted portion of the internet not visible to the general public via a traditional search engine such as Google. Also known as the darknet, the dark web constitutes a large part of illegal activity on the internet. Using a reliable VPN provider helps keep you safe when you access marketplaces on the dark web. A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities.
Run Antivirus/Anti-Malware Software
To appreciate why some users turn to the Hidden Wiki rather than Google, it’s important to understand the distinction between the surface web and the deep web. The surface web consists of all websites indexed by traditional search engines like Google, Bing, or Yahoo. This includes sites with publicly accessible content, such as news portals, blogs, and social media platforms. In contrast, the deep web encompasses parts of the internet not indexed by standard search engines. For developers and site operators, hosting on the dark web requires privacy, uptime, and resistance to attacks.
- Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
- It indexes a wide array of content, including both legal and illegal sites.
- It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are.
- However, it’s very difficult and would require extensive resources, meaning that the average person’s identity is unlikely to be uncovered.
- In the simplest of terms, both deep and the dark web are a subset of sites on the internet that are not indexed for traditional search engines.
Resources
The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. You can choose the best darknet (.onion) website that suits you and start surfing. For safer browsing, it is highly recommended to also use a VPN and antivirus software.
The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information. I2P uses one-way tunnels, so an eavesdropper can only capture outbound or inbound traffic, not both. If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed). Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable. As long as users take the necessary precautions, no one knows who anyone else is in the real world. Users’ identities are safe from the prying eyes of governments and corporations.
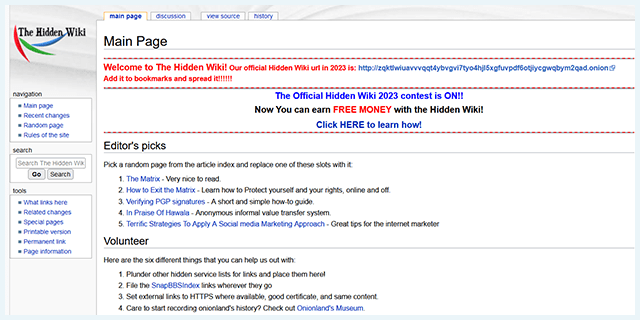
The dark web version of Facebook isn’t malicious, but if you log into it, it will keep your data. If we need a website to get links to other hidden sites, we will choose Hidden Wiki. But if you are thinking you can find links to the deepest part of the dark web using this site, it’s not that simple.

Best Dark Web Sites

There are currently several online darknet markets, but they tend to be incredibly volatile due to government intervention. If you do need to access a dark web website for legitimate reasons, you can check directories like The Hidden Wiki to help find options. However, engaging in any illegal activities, such as buying illicit goods, remains against the law, just as it is on the surface web. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals.
These malicious sites may attempt to steal your personal information or compromise your device’s security. If you suspect you’ve clicked a dangerous link, immediately disconnect from the internet, run a full malware scan, and change any passwords that may have been exposed. Because the Hidden Wiki aggregates many links, it often contains outdated or malicious URLs disguised as legitimate ones.
Blockchain uses a shared and unchallengeable record that authorized members can only retrieve. The network members rheostat what info each member may grasp and what actions they can take. Nodes store and propagate the network payments’ state efficiently, going straight from one person to another. BTC is the first and most extensively known digital cryptocurrency created in 2009 by an unknown person using the codename Satoshi Nakamoto. The transaction of this currency is made with no banks or without paperwork and can be used to purchase stock anonymously.
Use The Tor Browser
Then get a VPN to help protect your privacy on dark web websites or wherever you browse online. It’s a bit of a contradiction to talk about search engines for dark web sites because, by definition, these are not sites that get indexed by traditional search engines. Many dark web search engines on the darknet suffer from spam, because these spammy sites want to be indexed and found by the search engines as opposed to genuine onion sites. Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky.
Ultimately, your safety on these sites is your responsibility, so please keep your wits about you as you navigate. The Tor Project’s .onion site provides access to resources for downloading and using the Tor network, which facilitates anonymous communication and browsing. Tor, used by millions of people daily, routes traffic through a global network of over 6,000 volunteer-operated relays to protect users’ privacy. Also, only use .onion links from legitimate sources like The Hidden Wiki. However, make sure you’re careful which links you click on — some of them lead to sites that contain illegal content and services.

What You Need To Securely Browse The Dark Web
Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services. In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy.
One can also find drugs, crime services, stolen cards, and other illicit activities being offered by hackers. Despite its reputation, the dark web isn’t solely defined by illicit marketplaces or nefarious activity. Hidden networks also host a range of resources that can inform, educate, and support individuals who value anonymity. From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web. Ensuring that the onion links you follow lead to the intended, trustworthy destinations can be a constant challenge on the dark web. The complexity and randomness of onion addresses make it easy for scammers and malicious actors to create spoofed versions of popular sites.
Navigating .onion sites requires the Tor Browser, specifically designed for privacy and accessing the dark web. Follow these straightforward steps to set up Tor and begin searching safely. Onion websites use onion routing, a technique for encrypting and anonymizing data transmitted over the Tor network. The name “onion” comes from the layered structure of the encryption, similar to the layers of an onion.