This strategy includes calling out those states and publicly attributing their actions where we believe it is in the best interests of the UK to do so. We will not shy away from taking the tough decisions necessary to keep us all safe. This will help forces investigate cybercrimes, support local businesses and local victims and provide the advice and care they need. It will also help local law enforcement to deter potential cybercriminals before they get involved in crime. How darknet actors migrated from IRC forums to Telegram networks in 2025. On the brighter side, you can use the dark web to generate crime reports or publish articles on sensitive but legal topics to expose a company or government’s wrongdoings.
Extreme Pornography And Obscene Publications
Thus, sites on the Dark Web can be visited by anyone, but it is very difficult to work out who is behind the sites. And it can be dangerous if you slip up and your identity is discovered. In today’s digital era, where information is constantly on the move across all digital platforms, an…
Number Of Active Dark Web Marketplaces
A hard disk drive (HDD) is an internal or external computer component that stores data, such as the operating system, applications, and user files. HDDs are “non-volatile” storage devices, meaning they retain stored data even when power isn’t being supplied. A domain name is an internet resource that is universally understood by web servers and online organisation. It provides all pertinent destination information and is used to access an organisation’s web-based service. The top level domain (TLD) is the part of a URL which follows the dot, e.g. ‘com, net’. A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other.
Meanwhile our company intranet is hidden from search engines, and requires a password. You can browse to it if you know the URL, but it won’t appear in a Google search. In March 2015 the UK government launched a dedicated cybercrime unit to tackle the Dark Web, with a particular focus on cracking down on serious crime rings and child pornography.
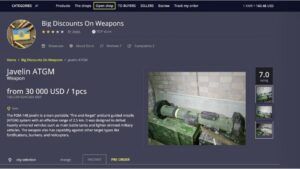
Awazon Market Link And Access Guide 2025

Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims. It is one of the most active and up to date markets and always provides new and updated malware and data. The punishment you receive for accessing certain websites on the dark web will depend on the content contained within said site and what you use it for. For example, the punishment you receive for buying or selling illegal drugs on the dark web will differ compared to accessing or publishing indecent images.

UK And The Dark Web – Here’s How To Check If You’re On There
Before joining PCMag, I wrote about tech and video games for CNN, Fanbyte, Mashable, The New York Times, and TechRadar. I also worked at CNN International, where I did field producing and reporting on sports that are popular with worldwide audiences. Finding real dark web links is possible via some clear web forums or social platforms like Reddit, though it’s just as easy to come across phishing links containing malware or links to scam sites. Always use an abundance of caution when interacting with anything or anyone on the dark web.
This scale is why newspapers and mainstream news outlets regularly trot out scare stories about ’90 percent of the internet’ consisting of the Dark Web. They are confusing the generally dodgy Dark Web with the much bigger and generally more benign Deep Web. And when you consider how many pages just one Gmail account will create, you understand the sheer size of the Deep Web. Thus the ‘Deep Web’ includes the ‘Dark Web’, but also includes all user databases, webmail pages, registration-required web forums, and pages behind paywalls. There are huge numbers of such pages, and most exist for mundane reasons. Hackers stole the data and threatened to upload it to the web if the site did not close down, and they eventually acted on that threat.

Child Sexual Offences And Indecent Images Of Children
- You can also start entering as little information as possible when signing up for online services or shopping.
- This layer is intentionally hidden from the general public and can only be accessed with specific software, settings, or authorisation.
- ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users.
- If the darknet is the hidden infrastructure, the dark web is the collection of digital destinations that reside on it.
- For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”.
- Never log in with your real name or reuse passwords from other accounts.
Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorised activity, and consider enrolling in a credit monitoring service. Additionally, report it to Action Fraud, the National Fraud & Cyber Crime Reporting Centre for further protective measures. The dark web and the browsers used to access its sites are not illegal.
Phishing Campaign Abuses Cloudflare Tunnels To Sneak Malware Past Firewalls
The decision of whether to charge ‘making’ under section 1(1)(a) of the PCA, or ‘possessing’ contrary to section 160 of the CJA will often depend how the images came to be located on a device and how accessible they are. The offence can only be committed as amended (i.e. by proof of a single initial communication or meeting) if that communication or meeting took place on or after 13 April 2015. Prosecutors should be careful to apply the provisions which were in force at the date an offence was committed.
Survey of active darknet marketplaces in 2025, strategy for threat hunters, niche trends and takedown impacts with metrics. Moreover, the dark web is a small portion of the deep web that is unavailable on search engines, making it difficult to monitor. Even though the dark web is famous for its illegal use, it is not controlled by a single person or organization. But your ISP will only know you are using Tor and cannot see what website you are visiting with it.
Developments in technology have also created a new landscape for controlling, sexually-motivated or other forms of interpersonal relationship offending. A charge of conspiracy under section 1(1) of the Criminal Law Act 1977, or the common law offence of conspiracy to defraud, may also be appropriate. Where there are a number of suspects allegedly involved in an online fraud, a statutory conspiracy under section 1 of the Criminal Law Act 1977, or common law conspiracy to defraud may be appropriate.
Legal And Illegal Activities
- It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims.
- Look no further if you want good music while navigating the dark web.
- The deep and dark web may sound similar, but they are not the same entities.
- It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications.
- The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures.
Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing. If you need a way to organize as an activist or you want to discuss censored topics with others, my first suggestion is to stick to offline meetups. The second, less secure option is to use encrypted messaging apps with ties to specific non-profit or activist organizations.
Facebook Onion Site
The Obscene Publications Act 1959 (‘OPA’) was amended to deal with electrically stored data or the transmission of that data. Transmitting comments to another person in the context of an internet relay chat is publication, even if there is just one recipient and one likely reader of the article. If the publication is obscene, prosecution under the OPA can be considered. For further guidance, prosecutors should refer to the prosecution guidance Obscene Publications.