When your card details are found, we immediately send an alert, allowing you to quickly take action, such as freezing your account or updating your card information. These criminals released the details of 740,858 credit cards, 811,676 debit cards, and 293 charge cards. The data dump disaster includes some complete names, expiration dates, CCV and unique email addresses. Detecting and preventing dark web credit card fraud can be difficult since the dark web is, by nature, hidden. By using specialized tools cybersecurity professionals can track these illegal activities and alert financial institutions of potential threats. This article will explore credit card theft on the dark web, explain how criminals obtain and use stolen data, and explain how to detect and prevent credit card fraud.

Kaspersky: 98% Of Cybersecurity Experts Seek Improvements To Maximize Protection
Equifax credit monitoring & ID theft protection features for one adult. The hackers disrupted claims processing for months and stole extensive data including names, contact info, Social Security numbers, and medical records. UnitedHealth began notifying affected individuals over the summer and cooperated with government regulators on the response. A U.S. state government agency fell victim to a multi-stage cyber intrusion enabled by leaked employee credentials.
How Technology Is Evolving To Counter Card Fraud On The Dark Web
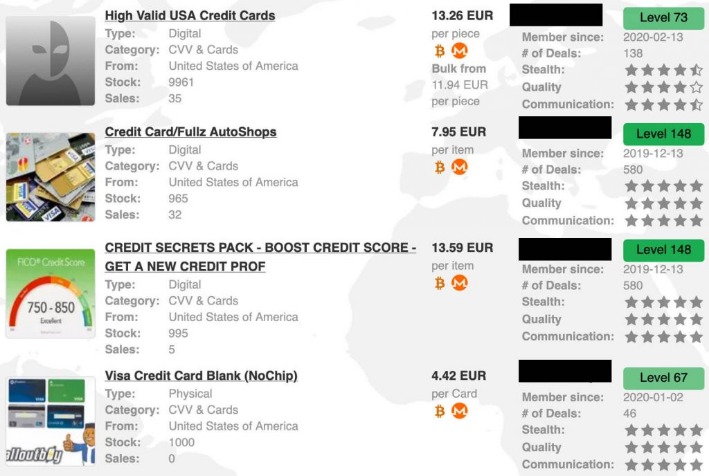
Not only is stealing someone’s credit card illegal but then selling that is also illegal, and then someone else using the stolen credit card is illegal too. Card Shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information. These platforms serve as hubs for cybercriminals to easily buy and sell compromised payment card details, including credit card numbers, CVV codes, expiry dates, and cardholder information.
Data Breaches That Occurred In May 2024
Carding forums act as central hubs for cyber criminal activity—particularly for promoting websites and Telegram channels that sell stolen credit card data. In other words, these forums serve as advertising platforms for illicit services. Occasionally, data dumps containing credit card details or other sensitive information are also shared directly within the forums. In addition to just selling credit card details, some threat actors offer a “complete package” often referred to as “Fullz”. Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft.
The threat actor’s marketing strategy involves leaking a large number of credit cards to attract potential clients from hacking and cybercrime forums. This move is likely to increase the platform’s popularity and draw in new customers. Some vendors offer a “complete package” known as “Fullz”, which includes full personal details as well as financial details like bank account information or social security numbers.

While payment details were masked and not usable, the breach involved basic contact information, dates of birth, order histories, and possibly reference numbers tied to M&S credit card and Sparks Pay accounts. Some criminals organize stolen card data by ZIP code, according to Novak, “because it makes it harder to conduct fraud detection,” he says. This is because criminals can purchase cards to use in their own geographical locations to limit the chances that their transactions will be flagged. Cybercriminals tend to rely on cryptocurrencies for their online transactions—for example, when purchasing stolen card data. As much as 95 percent of dark web transactions are conducted via cryptocurrencies—primarily Bitcoin—which allow criminals to transfer money without revealing their identities, according to Wilson. This activity is having an impact on those whose data has been compromised.

Second Helping For Would-be Fraudsters
Instead of card numbers and CVVs, criminals steal usernames and passwords that they’ve gathered either through phishing or malware. They can then sell the account credentials to a buyer who can log in and drains the funds, or the vendor can transfer the requested amount of money from the victim’s account to the buyer’s account. The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB.
Healthcare Sector Breaches
- Unlike other types of stolen data—such as email lists or personal information—carding exists as its own distinct niche within the cyber crime ecosystem.
- Employee and vendor data were affected, with at least one confirmed case involving a Maine employee whose name and Social Security number were compromised.
- The breach severely damaged the company’s reputation, led to over 20 lawsuits, and forced NPD to cease operations.
- Enter your email(s) to receive a free exposure report detailing what information criminals have in hand and learn what you can do to protect yourself.
Stolen credit cards are also harmful to the businesses from which they were stolen in the first place. Customers whose payment information was stolen are less likely to want to continue doing business with your organization after a hack and your organization may sustain long-lasting reputational damage. While consumers are typically protected from direct financial losses, dealing with credit card fraud is incredibly disruptive. Some threat actors even run automated validation services that check card numbers before the sale, guaranteeing their buyers a certain percentage of “live” cards.

Decoding Credit Card Fraud On The Dark Web
Implementing a 3-D Secure ACS solution, like Outseer 3-D Secure, fortifies the fraud prevention strategy. This EMV® 3-D Secure ACS delivers a secure, frictionless digital shopping experience, providing a multi-layered defence against unauthorized transactions. By adding an extra layer of authentication, financial institutions reduce the risk of fraudulent activities during transactions. This proven technology, seamlessly working in the background, analyses transaction data and authenticates users in real-time, ensuring only legitimate transactions proceed. The hackers used a combination of phishing and malware to gain access to the company’s systems. They then extracted sensitive information, including credit card numbers, expiration dates, and security codes.
Dark Web Prices For Stolen PayPal Accounts Up, Credit Cards Down: Report
Customers have been prompted to reset passwords upon their next login. The attack caused disruptions to online purchases and affected store inventories. M&S joins Harrods and Co-op as part of a broader campaign targeting UK retailers. Scattered Spider has been linked to the attacks, though a group known as DragonForce also claimed responsibility. According to cybersecurity firm Radware, the group has conducted distributed denial-of-service (DDoS) attacks and website defacements, primarily targeting Thai government and military domains.
New Report On James Comey Suggests ‘ongoing Conspiracy’ Against Republicans, John Solomon Argues
- To pull off these credit card scams, D2 and other fraudsters would sign onto sites on the dark web and simply pay a small fee—as little as $35 — for victims’ credit card information.
- I agree to Money’s Terms of Use and Privacy Notice and consent to the processing of my personal information.
- Companies such as my #1 pick, Identity Guard, can monitor your Social Security number (SSN) and alert you if it is being sold on the dark web or being used to open an account.
- In an e-skimming attack, also known as Web-skimming or Magecart attack, adversaries inject malicious JavaScript code into website payment processing pages to steal payment card details from customers.
- This move is likely to increase the platform’s popularity and draw in new customers.
- Fujitsu proactively isolated the affected systems and launched an investigation to assess the scope of any data exposure.
According to Security.org’s 2021 Credit Card Fraud Report, users with enabled alerts were more successful in preventing money loss than those without. Unauthorized charges were not blocked for 81% of users who didn’t have the alerts turned on. Card scammers and thieves are skilled at finding the existing vulnerabilities within payment systems. Becoming familiar with their techniques can help you retain control over your money. Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar. Adding fullz to a card purchase increases the price by about $30 for a physical card and under a dollar for digital card info.
Hathway Cable & Datacom Ltd Security Breach
Follow our recommendations to secure your information, such as notifying your bank and updating security settings on your accounts. We monitor your Equifax credit report, provide you with alerts, and help you recover from ID theft so you can focus on living your financial best. Defending the world from cybersecurity threats through continuous compliance. Once inside, they harvested additional passwords and escalated privileges, ultimately stealing sensitive host and user data which was later posted on a dark web marketplace. While no wider computer network breach was found, the attack underscored the risks of credential theft even in highly secured environments.
The incident resulted in the exposure of approximately 2.7 billion records, including sensitive information such as Wi-Fi passwords, IP addresses, and email addresses. Genetic testing company 23andMe disclosed a data breach that occurred between April and September 2023, affecting nearly 7 million users. Hackers accessed sensitive data, including health reports and genetic information. A ransomware attack on Toppan Next Tech (TNT), a third-party data vendor, potentially compromised customer information from Singapore’s DBS Group and the Bank of China (BoC) Singapore branch.
Post the dismantling of Joker’s Stash, cybercriminals displayed adaptability by establishing new marketplaces to fill the void, highlighting the resilience of criminal enterprises. This adaptability underscores the ongoing challenge faced by financial institutions in combating the ever-evolving threat of dark web credit card marketplaces. Much like the situation after Silk Road was taken down, out of the ashes of Joker’s Stash, we have seen dozens of new carding data providers crop up, some specializing in particular regions or types of card data. These days, criminals use a variety of methods to steal credit card numbers without ever needing a physical card. Learn about some of the most common techniques and join LifeLock Ultimate Plus for credit card transaction alerts and other fraud detection and identity theft protection features.
These cards are then used by cybercriminals to make online purchases, including buying gift cards, that are hard to track back to them. Carders tend to target specific sites that don’t have VBV or other protections against fraud. For fledgling criminals who don’t know how to use stolen credit cards, there are plenty of free and paid tutorials for carding on the dark web. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address.