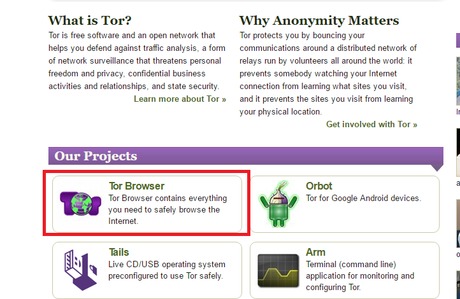
Even if they aren’t actively malicious, they might still have weak security or expose you to threats. Additionally, make sure that you only download the Tor Browser from the official website. Open the VPN app and connect to a nearby server before launching the Tor Browser, and that’s it! You can download the VPN app from the provider’s official website or your device’s app store. Run the setup file and then simply follow the on-screen instructions.
Tools And Precautions
Read reviews, check ratings, and be cautious of scams or fraudulent activities. Securely make payments using cryptocurrencies like Bitcoin, and maintain anonymity throughout the process. Install the VPN and connect to a server before opening Tor to prevent IP leaks. The nearest server will typically provide the fastest and most stable connection speeds. For more information, check with reliable resources like the Tor Project and privacy-minded communities.

Tools And Techniques For Dark Web Monitoring
This guide is provided for informational purposes only and does not encourage or endorse any illegal activities. It is crucial to prioritize online safety and adhere to legal boundaries while using the internet. Once you have installed the Tor browser, you are ready to access the Dark Web.
- Before you go much further, it’s important that you close out of other applications and software that offer malicious users on the dark web an entry point into your device or network.
- Be cautious of random or obscure links — these could lead to dangerous or malicious websites.
- A good antivirus software can detect, quarantine, and remove threats before they can damage your device or acquire any sensitive information.
- Browse the search results, clicking on each listing to view the product in more detail.
- In other words, purchasing bitcoin via a service that requires you to complete know your customer (KYC) identification does not preclude you from spending those coins on the darknet or elsewhere.
Legal Trouble
Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web. While the process is not overly complicated, it demands attention to detail, adherence to best practices, and an understanding of the risks. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for. Once connected to Tor, you’re ready to begin exploring the dark web.
Always remember, your safety online depends significantly on personal responsibility, informed decisions, and proactive application of security tips. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape. The most common tool for accessing the Dark Web is Tor (The Onion Router).
You can find both legal and illegal websites/activities on the dark web, as it isn’t regulated in any way. Before accessing the Dark Web, it’s recommended to use a Virtual Private Network (VPN) to mask your IP address and encrypt your internet connection. A VPN adds an extra layer of security and ensures your online activities remain private. Additionally, it’s essential to use the Tor Browser, which is specifically designed for accessing the Dark Web. Accessing the Dark Web safely in 2025 demands vigilance, preparation, and strict adherence to security best practices. By carefully following the safety procedures outlined in this guide, you minimize your risk of encountering malware, fraud, or legal troubles.
How To Install Tails OS
Additionally, ensure that the VPN service has a wide network of servers in various locations to offer you more options for server locations. Before accessing the Dark Web, carefully weigh the potential benefits against the risks involved. Ensure that you are aware of the legal implications, take necessary security precautions, and approach any transactions or interactions with caution. Accessing the Dark Web offers both benefits and risks that users should consider before venturing into this hidden realm.
Cool Augmented Reality Examples To Know About
Use them with PGP encryption for secure communications and Tails OS to isolate sessions, ensuring sources remain protected in high-stakes environments. Ahmia suits cautious users needing clean, multilingual searches, while Torch is better for power users tolerant of outdated UIs and manual verification, but it poses higher risks of scams. Avoid clicking unverified links from results, and cross-check with directories to prevent phishing. This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design. To safely access NotEvil, first download Tor Browser from the official site and connect via a reputable VPN like NordVPN for added IP masking.
VPNs And Proxies: Practical Alternatives
Its smaller index (~5,000 sites) is a deliberate choice, focusing on quality and active .onion sites rather than casting a wide net like Torch. DeepSearch’s lightweight design ensures fast performance on Tor, and its open-source codebase fosters trust through community audits. In 2025, I revisited The Hidden Wiki to locate a SecureDrop instance for a whistleblower story. The “Whistleblowing” category pointed me to an active .onion link, but I had to confirm its authenticity through r/onions to avoid a clone. The directory’s structure saved time, but its inconsistencies required extra legwork. Frequently mimicked by clones and scams, the “authentic” Hidden Wiki requires verification via trusted Tor forums (e.g., r/onions on Reddit).
This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.

What Is The Dark Web And Tor?
The surface web is what the average daily internet user interacts with the most. Search engine results from Google, Bing, and Yahoo, public websites, social media, and anything else that’s indexed and publicly available is considered a part of the surface web. While there are other dark web browsers, they’re generally unreliable, unsafe, and complicated.
Step 4: Automate The Monitoring Process
When browsing the dark web on mobile, finding what you’re looking for can be tricky. Dark web search engines are the gatekeepers to the Tor network’s hidden corners, empowering users to explore what’s intentionally unindexed. Businesses can scan for leaked data or cyber threats using premium engines like Haystak for monitoring forums and marketplaces. Integrate with tools like dark web monitoring services for alerts on credentials or IP theft.