There’s also a much more sensitive proposal that could only proceed with government approval. Companies could train AI models on fake child sexual exploitation images to build more sophisticated detection systems. Without proper safeguards, though, that route could result in companies developing AI models that are even better at producing even more lifelike images.
How Do I Open Onion Links?
It can do this by creating an encrypted internet connection with a server run by the VPN provider. Back in 2018, Pornhub jumped on the bandwagon by introducing its own product, VPNhub. To protect users’ privacy, the Tor mirror has also disabled certain features, including the ability to login as a registered user, and video uploading. OnionName lets you generate an .onion domain name that starts with a specific keyword — like onionamev33r7w4zckyttobq3vrt725iuyr6xessihxifhxrhupixqad.onion/, which is OnionName’s dark web link.
In AI-Generated ‘Undressing’ Images Move from Niche Pornography Discussion Forums to a Scaled and Monetized Online Business, researchers note that Telegram is often the source of the creation and dissemination of SSEM technology. Every app this dangerous man used to prey on children could have prevented the exploitation from happening. In a February 2024 study, Tech Platforms Used by Online Child Sexual Abuse Offenders, Telegram was noted as the #1 most popular messaging app used to “search for, view, and share CSAM” by almost half of the offender respondents (46% Telegram, 37% WhatsApp).
The youngest was born in 2006, while the oldest was in their seventies. A total of 36 countries, including Britain, joined forces to dismantle the platform. In March, police conducted coordinated raids across 31 nations in what Europol’s Guido Limmer described as the “largest operation ever” of its kind. This January, the FBI was part of another international operation that took down the cybercrime marketplaces known as “Cracked” and “Nulled”. According to DOJ, Cracked and Nulled provided access to “stolen login credentials”; personal “identification documents”; and “hacking tools”– impacting at least 17 million victims in the U.S.
TikTok Puts Hundreds Of UK Content Moderator Jobs At Risk
After establishing trust and committing to treatment, individuals who are sexually attracted to children can gain the ability to consistently regulate their impulses. The favourable confidentiality legislation in Germany, which prohibits therapists from disclosing planned or actual child abuse offences, naturally strengthens this trust. Project evaluation shows that post-treatment recidivism is lower among individuals who commit contact offences as opposed to child sexual abuse material users. This demonstrates the need to develop tailored interventions based on the offender’s background and behaviour.
Internet Platforms
Thus, staying connected to a VPN when you access these sites is vital. Dark.fail is an easy-to-use .onion platform equipped with a status checker that tracks website uptime. The site offers access to PGP-verified URLs and runs free of JavaScript or tracking. This platform’s library of websites currently totals 50, which may not sound impressive until you consider that all the links are active and popular.
- This space for private free speech also carries the risk of exposing you to harmful content.
- In a statement, the national center said it did its best to route reports to the correct jurisdiction.
- In addition to targeting human trafficking, law enforcement officials are finding that they can tap Memex to crack down on other, related crimes, including trafficking in guns and drugs.
- Facebook’s dark web version allows users to access the site where it is banned or restricted.
Illegal Markets
- Accessing the dark web is legal in itself; the nature of the activities you engage in ensures it stays that way.
- That’s why it’s important to verify links through trusted directories and proceed with caution.
- Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines.
- Users could exchange funds online without sharing credit card numbers or other identifying information.
- When you’re dealing with sensitive information, nothing feels truly anonymous or private.
- The research project was granted full ethical approval by the Science Technology Engineering and Mathematics Ethics Committee at the University of Birmingham ERN_ E, and the Psychology Research Ethics Committee at the University of Bath.
Offenders were also documented sharing advice and even AI models fed by real images with each other. Repetitive pornography use has similar effects to substance addiction31. Many people continually use CSAM and display addictive behaviours32, and the intensity of CSAM use often has properties that users call addictive33. In the search engine data, we notice that users who seek help often refer to their condition as ‘child porn addiction’. Understanding the commonalities between CSAM use and addiction is beneficial to prevention and treatment.

Advocates defend the dark web as a last potential refuge against oppressive governments and communities. This search engine’s mission is to be leaders in providing services on the deep web, protecting the anonymity of each user. In addition, they share information of great importance, about the Tor network and the Tor project.

Is Using The Tor Network Illegal?
Blockchain even has an HTTPS security certificate for even better protection. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. The dark web is a hidden part of the Internet that the majority of Internet users do not think about or engage with, with the standard activities happening there varying greatly from that of the mainstream Internet. If you are engaging in the use of the dark web and have been charged with Internet sex crimes, it’s critical to work with an experienced sex crimes attorney who can help you protect your rights. As well as studying the security precautions taken by online CSEA offenders, researchers have considered the types and nature of interactions between members of these online communities in the Surface Web.
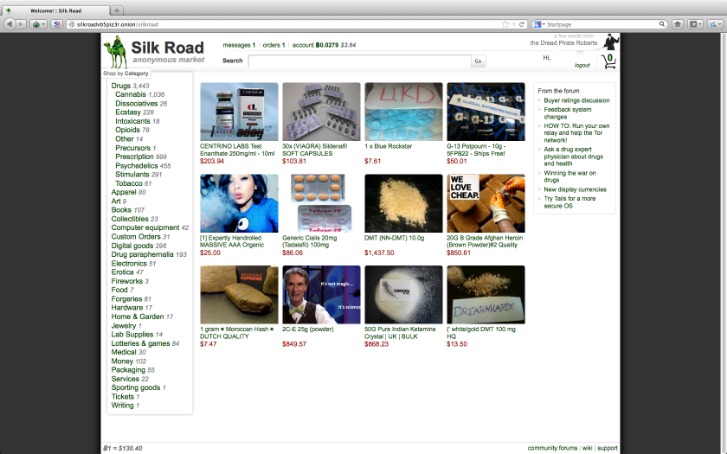
The WeProtect Alliance’s 2019 Global Threat Assessment report estimated there were more than 2.88 million users on ten forums dedicated to pedophilia and paraphilia interests operating via onion services. Some countries and ISPs may try to prevent access to DuckDuckGo’s direct link. This is a public domain, where you can talk about anything from crony capitalism and animal liberation to pandemics. Speak your mind here without fear, as onion links are immune to censorship.
Violent Online Groups Extort Minors To Self-Harm And Produce Child Sexual Abuse Material
But despite an increase in productivity and the availability of new tools and technology, the IWF’s humble resources remain overwhelmed by the sheer scale of the task it faces. Of the 105,047 URLs flagged for removal by the IWF’s 13 analysts, 82 per cent were from image hosting websites. Susie Hargreaves, the charity’s CEO, criticised these sites for refusing to engage, adding that they have shown “little regard to providing safe networks, or relieving the suffering of child victims”.
Stay Up-to-date With The Latest News And Additional Resources
U.S. authorities have identified the dark web as a collection of hyperlinked services on the dark net only accessible through specialized technologies. Internet browsers use the dark web’s online identity protection for purposes that range from anti-authoritarian regime reforms to selling drugs. Since you cannot access a library of dark web links using the regular Internet, you can check out platforms dedicated to indexing these sites, like The Hidden Wiki. With NordVPN’s double VPN feature, your traffic is routed through two servers for double encryption.

Best Dark Web Sites To Know In 2025 – Detailed List
Research on the darknet is not easy and requires a combined effort from LEA, academia, technology service providers, and non-govermental organisations. The scant research (McMahan et al. 2023) suggests that individuals who commit sexual offences via the darknet can be assessed using available assessment measures but may have different profiles from clearnet users. By better understanding users of CSAM darknet sites, practitioners and LEAs would be better able to address the needs and risks posed by this subgroup of individuals at risk for sexual offences. We hope this review provides researchers and practitioners alike with an overview of the darknet and encourage research to better understand users of darknet CSAM forums, so as to ultimately inform management and prevention efforts.
Torch Search Engine
That means you may violate copyright laws while downloading books, so use a VPN to protect yourself from any legal repercussions if you have a dire need to use it. Sci-hub is a helpful dark web platform for those looking to access important research blocked by a paywall. You can access almost any published paper that would have otherwise been hidden behind a paywall. The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Therefore, you will always find updated search results while using this service.
DARPA chose law enforcement efforts to disrupt human trafficking as a concrete cause around which it could quickly develop and deploy its new approach to searching the Internet. White is confident that Memex technology can likewise be applied to any type of investigative effort, including counterterrorism, missing persons, disease response and disaster relief. Dark Web sites have, of course, attracted DARPA’s attention because they are good candidates for human trafficking activity. As a result, White and his team are developing a “Dark Web crawler” that explores the Tor-accessible, peer-to-peer areas of the deep Web and has thus far done much to enlighten the researchers as to the extent of dark Web activity. Whereas it was once thought to consist of 1,000 or so pages, White says there could be anywhere between 30,000 and 40,000 dark Web pages. “Just finding these pages and seeing what’s on them is a new aspect of search technology,” he says.