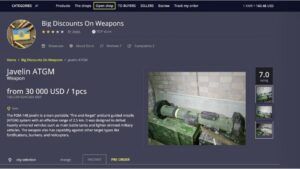
Kilos specializes in locating and accessing dark web markets, many of which are focused on illegal drug trades. Unlike many search engines that avoid the darkest corners of the web, Kilos actively delves into these areas without filtering search results. While this unfiltered approach propelled Kilos to prominence as a top black market search engine, it also makes it a potentially risky gateway to dangerous sites. Although it’s not a search engine, it offers a categorized directory with indexed links to .onion web pages.
When you purchase using links on our website, we may earn an affiliate commission at no extra cost to you. Report via the engine’s community mechanisms, like Ahmia’s GitHub for blacklisting or NotEvil’s volunteer reports, or submit to Tor Project forums anonymously. They operate on Tor, encrypting queries end-to-end, but users must still enable “Safest” mode and use VPNs to prevent leaks. This makes them superior for privacy advocates, though opaque operations in some (e.g., Torch) can raise concerns. To safely access NotEvil, first download Tor Browser from the official site and connect via a reputable VPN like NordVPN for added IP masking. Tor’s mobile browser, with 20% of users by 2025 (Tor Project metrics), drives demand for responsive, low-bandwidth engines.
Key Features Of The Dark Web
It offers both free and premium services, with the premium version providing additional features and more detailed results. At the end of the day, searching on the Deep Web should be done cautiously. Some Deep Web search engines discussed here are perfectly okay to explore, but once you get into the Tor world, your online guard should be up. For example, most public records are stored in databases and not on individual static web pages. This makes it “invisible” to Google, but we can get this information from Deep Web search engines.
CSO30 Winner Vishwanath Nair On Balancing The Tech And Human Element Of Cyber Defence
The directory’s structure saved time, but its inconsistencies required extra legwork. The open-source transparency gives me confidence, and its clearnet access is handy for quick checks (though I always use Tor for serious searches). I’ve avoided countless dark web traps thanks to its filtering, but the smaller index frustrates me when researching niche topics.

Top 7 Dark Web Monitoring Tools
Our browser extension blocks ads, malicious content, trackers, and scams— delivering a faster, safer and cleaner browsing experience and protecting your privacy. Always-on protection blocks malware, viruses, spyware, and ransomware without slowing you down. Unverified or misleading information on the Dark Web can lead to inaccurate threat assessments. Brandefense’s Threat Detection ensures reliable and actionable intelligence, minimizing the risks of acting on false data. It is designed to ensure user anonymity while offering access to a diverse array of information available on the dark web.
The Hidden Wiki (2007) revolutionized dark web navigation by introducing the first structured directory, categorizing .onion links into forums, marketplaces, and services. It became the dark web’s de facto entry point, akin to a digital yellow pages, but its manual curation limited scalability. Maintained by anonymous volunteers, Torlinks prioritizes secure, modern .onion addresses and updates its database monthly to weed out dead links. While it lacks keyword search, its clean design and focus on trusted sites make it a reliable starting point for beginners and pros. Launched in 2022, OnionLand is a modern dark web search engine that brings surface web polish to the Tor network.
Download Our AI Security Posture Management (AI-SPM) Enterprise Buyer’s Guide
Monitor and prevent security incidents against your suppliers, people, and brand with actionable alerts from the Dark Web. DarkIQ helps you identify cyber criminals before they attack so that you can prevent security breaches from happening in the first place. But retaining and attracting the Dark Web can be costly and difficult due to its heightened privacy in accessing content. KEY TAKEAWAYS Vulnerability management tools scan and detect weaknesses within the network that hac… It is advisable to use the best password managers that generate strong passwords and store them in a secure encrypted vault.
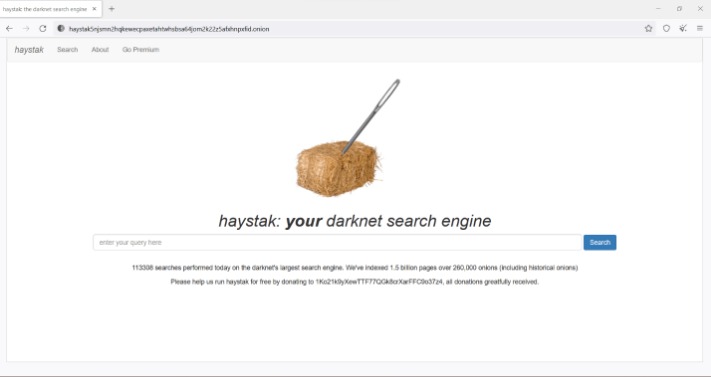
Beyond the Tor browser, consider using VPNs, encrypted communication tools, and secure operating systems. These tools add layers of privacy and protect against data leaks and surveillance. The dark web consists of websites that use encrypted .onion domains, which require specific software and protocols to access. Haystack is a dark web search engine designed with privacy in mind, similar to Duck Duck Go. It pulls data from different search engines, so it opens you to a world of endless possibilities.
- The dark web is intentionally hidden from surface web indexing, and to access it, you need a specialized dark web browser, like the Tor browser.
- For a lot of users, they will favor ease-of-use over security and connect directly from their standard workstation, but this has serious security considerations.
- Engines like Ahmia minimize this with no-log policies, but misconfigurations (e.g., enabled plugins) or correlated metadata can expose users.
- The best part of SearchLight is that users can try it for free for seven days.
- Do you know that your email and other personal information might be on Dark Web?
- Finally, the monitoring tools can act on catalogued data, applying rule sets to alert administrators or automatically perform remediation actions to prevent further compromise.
Best Unblocked Browsers To Open Blocked Sites
Trusted directories include Daniel’s Onion Directory, The Hidden Wiki, and TorLinks—all frequently updated with .onion links. Onion.live is a platform that tracks the status of dark web sites and provides trust ratings to help users verify site legitimacy. There is no point in scheduling a total scan of the Dark Web say, once a month because as soon as credentials on your network are published, your business is exposed. The best Dark Web scans spot protected accounts as soon as their details appear on a Dark Web forum, enabling users and account administrators to change login credentials immediately. If you find information about your employees on the Dark Web, you are lucky. However, this is a warning to tighten up your network security and enforce a password change on all system users through your access rights management system.
Multilogin are also known for protecting user privacy. Yes, you can still be tracked on the dark web despite its privacy features. Tracking can happen through IP leaks, browser vulnerabilities, or malicious exit nodes.
- The open-source transparency gives me confidence, and its clearnet access is handy for quick checks (though I always use Tor for serious searches).
- After in-depth analysis, it provides real-time information about the potential attacks targeting the organization.
- Tor provides source and path obfuscation across the internet and is sometimes used by hackers to cover their tracks.
- In his view digital footprint monitoring is a particularly valuable tool and will often include a dark web component.
- The dark web is a part of the internet not indexed by traditional search engines like Google.
Advancements In Search Engine Technology
Identity Guard uses your email address to scan the dark web for any compromised data. The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Tools like Flare empower your team to conduct reconnaissance on the dark web, scanning for stolen data and other information that might jeopardize your systems and networks. Torch—a portmanteau of “Tor” and “Search”—is a seasoned dark web search engine that was one of (if not) the first of its kind. Its large search library, speed, and commitment to user anonymity make it a preferred choice for many people who browse the dark web. The Tor browser is open-source and is used to access the dark web, where data is encrypted and routed through multiple relays before reaching its destination.
The search engine excels at indexing a wide range of content, from forums to marketplaces. Its advanced algorithms deliver accurate search results, helping you find relevant information quickly. NotEvil is particularly useful for research purposes, as it provides access to resources that are often overlooked by other deep search engines. DuckDuckGo’s dark web version brings the same commitment to privacy as its surface web counterpart. As one of the most privacy-focused search engines, it does not track your searches or store your personal information. DuckDuckGo is also known for its clean interface and straightforward functionality, which simplifies the process of searching hidden services.
How Often Should I Scan The Dark Web For Data Breaches?
You need to use a dark web browser—such as the Tor browser—to search and access the dark web. Dark web browsers are specially designed to connect to websites on the Tor network, where most dark web sites are hosted. Though you can search dark web indexes with some traditional browsers, you won’t be able to access the sites themselves. LibreY stands out by supporting dark web image search, text results, and torrent links, making it user-friendly and accessible for beginners looking to explore the dark web. The Kilos search engine is primarily used to find and access dark web markets where illicit drug transactions are one of the main activities. While many search engines steer clear of the dark web’s seedier elements, Kilos embraces it and doesn’t filter search results.

Do I Need A VPN To Use The Dark Web?
Webz.io crawls forums, sites, marketplaces, etc., in the Dark Web to transform web data into structured and standardized data feeds. It can also extract password-protected or encrypted illicit content, keywords, sites, entities, and more. Rapid7 helps you mitigate online threats with features like contextualized alerts offering a rapid response. It will also let you easily prioritize your mitigation efforts in order to reduce the investigation time and accelerate alert triage.
They facilitate privacy and allow users to find uncensored information, engage in secure communication, and research sensitive topics. Forest VPN is a crucial tool for anyone looking to access the dark web securely. By providing a private and encrypted connection, it ensures that your internet service provider and any potential snoopers can’t track your activity.