Many simply install free software for enabling anonymous communication and direct internet traffic through a free, worldwide, volunteer network consisting of more than seven thousand relays. The user’s location and the usage are hidden from anyone conducting network surveillance or traffic analysis. Most of these free software options make it more difficult for Internet activity to be traced back to the user, including website visits, online posts, instant messages, and other communication forms. Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats. Anyone considering engaging with these platforms must carefully evaluate potential consequences, exercise stringent security practices, and remain vigilant to minimize exposure to these significant hazards. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof.
Security Risks And Law Enforcement Crackdowns
Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets. This can be stopped if law enforcement agencies can break any link, particularly dark web marketplaces, in the chain. Hence, it should be the top priority to track these platforms and shut them down as quickly as possible.
There is a gray zone in which some sellers and buyers may not be easily distinguishable in transaction networks. For instance, there may be sellers that make a small amount of transactions, or spend more than receive, which we would classify as buyers. Despite consistent results, this clearly leaves space for refinements.
Types Of Darknets Used To Access The Dark Web
Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with. Wasabi is one of the most popular cryptocurrency wallets on the dark web. ZeroBin is a wonderful way to share the content you get from dark web resources.

Essential Security Tips For Using Dark-Web Marketplaces
When he’s not empowering PrivacySavvy’s readers to take control of their online security, Saheed enjoys distance running, playing chess, and exploring the latest open-source software advancements. To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead. The more proactive you are, the better you can protect yourself against identity theft and other cyber threats.
#1 Install A VPN
In fact, previous studies on DWM transaction networks have revealed crucial aspects of the ecosystem13,14,15. However, they have so far mainly focused on DWM users, without distinguishing between buyers and sellers, and neglecting the different weight that more active users may have in the system. The reason is that the operational structure of DWMs inherently hides the seller–buyer link, as all transactions are made through the marketplace. Buyers send money to the marketplace, which in turn sends the money to the seller. In this article, we explore the evolution of the digital black market. We first explore how the concept of currency evolved into a digital, anonymous form – a critical component of the modern vulnerabilities and illicit goods black market.
Hacker services against banks and other financial institutions are offered there. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. The dark web is a very popular platform for journalists, political bloggers and political news publishers, and in particular, those living in countries where censorship shields most of the internet.
Money Laundering
Most of the vendors guarantee that their products will live until the promised lifespan. Cryptocurrencies, while offering enhanced privacy, also present significant risks. Users face vulnerabilities like market volatility, scams involving fake escrow services, compromised wallets, or theft through phishing schemes targeting crypto transactions. Furthermore, inexperienced users unfamiliar with secure cryptocurrency practices are particularly susceptible to these threats, risking the loss of their entire funds. Given the explosive growth of these markets, organizations must prioritize proactive threat monitoring. Axis Intelligence provides dark web surveillance solutions that help businesses identify leaked credentials, fraud attempts, and malware risks before they escalate.
Common Scams And Fraudulent Activities On Darknet Markets
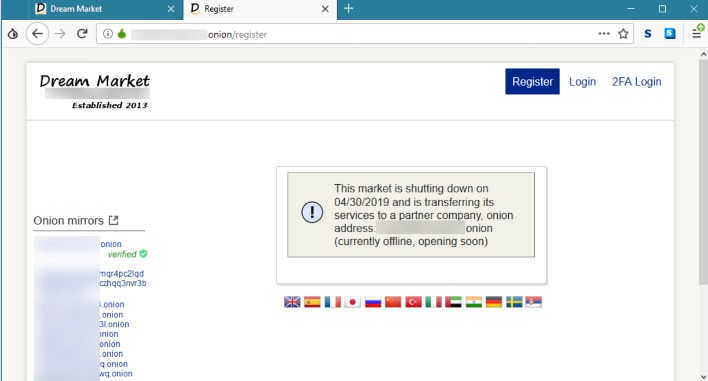
The vendors aren’t required to register or apply for a vendor account while using this platform. It ensures the buyer’s identity is kept hidden and accepts payments through cryptocurrencies, including Bitcoin, Litecoin, Ethereum, and Monero. The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. It’s a user-only marketplace, meaning you need to register to enter. During our tests for the research, we were able to register with a bogus email and a random username.
Impact On Businesses And Cybersecurity

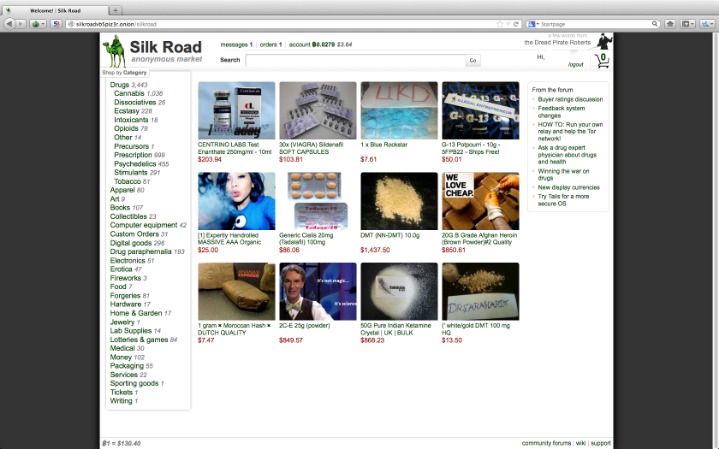
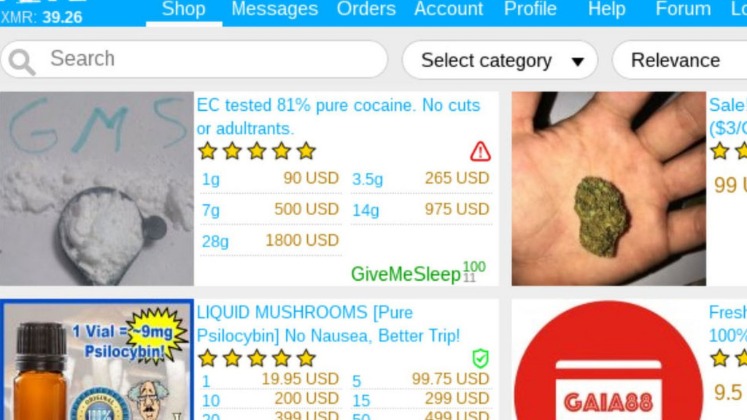
The technology behind the darknet is actively maintained and continues to evolve. Deep web marketplaces are online marketplaces where people can buy and sell illicit goods and services under the protection of the anonymity of the dark web. The goods and services on offer range from leaked credit card details, exploit kits, and hackers for hire to advertisements for hitmen services. The dark net is famous for being a hub of black market websites for buying and selling products and services. If you purchase something from such shops and make payment through conventional payment methods like your bank transfer, credit/debit card, or PayPal, you can be caught easily and face legal consequences. Transactions in these underground markets prioritize anonymity and security to evade detection.
Avoid downloading files, clicking on unfamiliar links, and sharing personal information. Additionally, do not attempt to buy anything on the dark web as most transactions are illegal and can lead to scams. However, engaging in any illegal activities, such as buying illicit goods, remains against the law, just as it is on the surface web.
- Tor stands for “the onion routing project.” It was developed by the U.S.
- While it’s a deep resource, it’s also illegal in many countries, because it may violate copyright restrictions, so check out the laws in your area before visiting.
- Law enforcement efforts are increasingly effective, and technological shifts are changing the way these platforms operate.
- Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection.
- By taking precautions and using tools like Forest VPN, you can explore this part of the internet safely.
For businesses and individuals alike, understanding these threats is the first step in securing their digital assets. However, combating dark web risks requires more than just awareness—it demands proactive and comprehensive protection. With advanced dark web monitoring, threat intelligence, and brand protection services, we help you uncover hidden dangers, prevent data breaches, and safeguard your reputation. Our platform ensures that your brand stays one step ahead of cybercriminals, giving you peace of mind in an increasingly complex digital landscape.
Others sell pirated eBooks, academic materials, and entire premium courses ripped straight from paid platforms. While hiring a hacker might sound like something out of a movie, it’s a very real threat. Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone. Want to get illegal drugs, fake passports, Trojan, or other cyber attack software?
This marketplace accepts payments via Monero but also supports the Escrow system. For businesses, the cybersecurity risks posed by Dark Web marketplaces are substantial. Data breaches, leaked credentials, and intellectual property theft are common occurrences.



