While no search engine can cover the entire dark web due to its decentralized and ever-changing nature, Haystak is a top choice for exploring its hidden content. TorlanD opens up access to a vast range of hidden content, allowing you to navigate the deep web freely without restrictions. Haystak boasts an impressive index of over 1.5 billion pages from more than 260,000 websites on the dark web.
Independent News Outlets And Investigative Journalism
You can even use a secure email provider or a burner email address whenever you visit the dark web. The website has a sleek design and interactive user interface, making it the most preferred choice in terms of user experience. You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop. In April 2016, its APIs were compromised, resulting in stolen messages.
From dark pool markets to escrow networks, this guide maps the underground economy. Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims. It is one of the most active and up to date markets and always provides new and updated malware and data.
Navigating Darknet Markets In 2025
The site doesn’t require an email verification, though it offers all the features and security that you want in a dark web marketplace. OnionLinks is a library of dark web links, most importantly, active links. Depending on your preference, you can find links in well-categorized groups.
Separate Your Real Life From Your Online Persona

Use PGP (e.g., GPG) to secure vendor messages and protect your trades. Use Tor Browser from torproject.org for safe onion routing—update regularly. Alphabay rose to prominence with 400,000+ users and $600M yearly trades, ending in a 2017 bust. The first major darknet market pioneered BTC trading, processing $1.2 billion before its 2013 shutdown.

My favorites are DuckDuckGo (usually the Tor browser’s default search engine), The Hidden Wiki, and Ahmia. Dark web operators use mainstream social media platforms to promote illicit goods. Advertisements for fake passports, stolen credit card dumps, and malware appear in private groups, often disguised with coded language. Once contact is made, vendors transition discussions to secure messaging apps to complete the transaction. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
These “onion” sites are only accessible on the dark web and bear the “.onion” domain at the end of the URL. This is no different from the “.net” or “.com” of the regular Internet. According to Kaspersky, Librarian Ghouls APT continues its series of attacks on Russian entities. A detailed analysis of a malicious campaign utilizing RAR archives and BAT scripts.

Tor Links
It offers both free and premium services, with the premium version providing additional features and more detailed results. Many free VPN providers lack basic security features and track your online activity, so they don’t offer much privacy. SecureDrop is an open-source platform that facilitates secure communication between whistleblowers and journalists.
News And Journalism
During testing, I confirmed it provides the same functionality as the regular site while adding Tor’s privacy benefits. The interface works smoothly, but it usually loads slower due to Tor routing. Adamant offers blockchain-based secure messaging without needing phone numbers or email addresses. The platform stood out during my testing for its commitment to anonymity — all messages are fully encrypted and stored on a decentralized network.
- Developers introduced advanced techniques, advertising subscriptions ranging from $100 to $20,000.
- The primary purpose of these tools is to render the code undetectable by security software.
- Onion sites are far safer to use as they are hidden deep within the deep web.
- These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers.
- Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though).
Improved Security Protocols
It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web.
Tweak Tor Browser Settings
There has been a shift toward the development and distribution of premium private solutions, which are becoming increasingly prevalent compared to public offerings. Insider threats may not always make headlines, but their impact can be devastating, often surpassing that of external attacks. Monitoring the dark web for indicators and implementing comprehensive prevention strategies can reduce these risks and safeguard organizations’ operations. As insider threats evolve in 2025, the dark web will continue to play a crucial role in their facilitation. Companies must adopt a proactive stance by expanding their dark web monitoring activities to detect early warning signs of insider risk. Watch for unexpected changes in system performance that could indicate malware.

Though there are other browsers with similar functionality, Deep Web statistics point to Tor as the most popular — with 5.92 million new downloads worldwide in 2023’s third quarter. These geopolitical dynamics intensify the complexity of cybercrime, creating multi-layered threats that affect both public and private sectors globally. Decentralized autonomous organizations (DAOs) even govern some of these markets. Such models ensure that the market remains community-controlled and resilient to outside interference. For several years, Yahoo was at the apex as the internet’s best web service provider, offering…
It includes all the essential productivity software, including MS Word and an email client. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN.
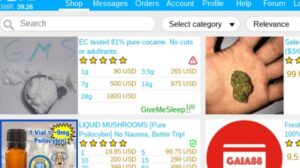
It’s divided into commercial links (from crypto services to gambling sites) and non-commercial links (like social media). As always, use Tor Links with care, as it includes onion links to dubious or illegal activity. Since these markets operate in hidden networks, scams and security risks are common. Knowing how to spot a legitimate dark web marketplace can help protect your privacy and funds. Many users value the protection that comes with keeping their identity hidden.