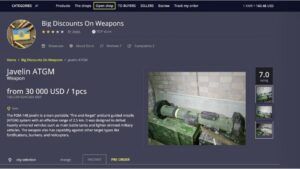
It’s recommended not to use new alternative links as they could just be planned exit scams. During our tests for the research, we were able to register with a bogus email and a random username. All that one can expect from a deep web marketplace when it comes to anonymity and security. The dark web has seen a dramatic rise in crypto asset draining services, with discussions about these malicious tools increasing from 55 threads in 2022 to 129 in 2024. Telegram has emerged as a central hub for these activities, facilitating a growing network of cybercriminals.
Best Free Firewall Software In 2025

Founded by Ross William Ulbricht in 2011, Silk Road quickly established itself as the go-to destination for illegal items, particularly illegal drugs. When the FBI arrested Ulbricht in 2013 for money laundering and drug trafficking, among other offenses, the criminal complaint revealed the marketplace had generated over $1.2 billion in just two years. But in December of that year, Russian authorities started blocking people’s access to Tor, describing it as a cover for illegal activities.
Deep Dive Into Darknet Markets Of 2025

Operators of these markets implement strict entry barriers, requiring encryption keys and multi-factor authentication. This focus on security ensures the anonymity of both vendors and buyers while making law enforcement infiltration more difficult. In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC). Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B. Exploit is widely regarded as a hotbed of the underground economy, where threat actors can secure stolen personal information, ransomware, botnets, and phishing kits. If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search engines or browsers, you’re likely on the dark web.
Data Breaches Through Contractors
However, this will likely lead to the rise of new, decentralized groups like RansomHub. They can also take advantage of legitimate software to hide their tracks. For example, YoMix is a bitcoin mixer used by the Lazarus Group to launder their stolen cryptocurrency profits, with a massive influx of laundered funds in 2023. Social media and gaming platforms are increasingly being used to recruit inexperienced hackers, further expanding these gangs’ reach. For example, Europol has warned the criminals will use coded messages and ‘gamification tactics’ to encourage minors to commit crimes.
RetailGPT Empowers Small Businesses To Compete In Digital Marketplaces

Vendors migrated to unstable alternatives such as Incognito and Bohemia, but none of these managed to consolidate trust or operational continuity. Cybersecurity tools like CybelAngel’s external attack management (EASM) platform can help businesses monitor the dark web effectively. By providing real-time insights into threats, these tools enable companies to safeguard their brand and prevent data breaches before they occur. The Tor project gained notoriety for enabling illegal marketplaces like the Silk Road, a black market taken down by the FBI in 2013—and countless cybercriminal service providers ever since.
Dark Web Trend Impact On Businesses And Individuals
Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof. Law enforcement agencies continuously improve their ability to trace transactions and monitor marketplace activity.
Are Businesses Legally Obligated To Monitor The Dark Web?

Kaspersky report states, Last year, the underground market for cryptors—tools used by cybercriminals to obfuscate malicious code and evade detection—grew significantly. Developers introduced advanced techniques, advertising subscriptions ranging from $100 to $20,000. Although there was a law enforcement sweep of BriansClub in 2019 that showed the platform had earned more than $126 million, the site continues to exist and advertise stolen data. This anonymity is very appealing for buyers and sellers, many of whom are experienced cybercriminals, and some low-level actors.
- Users and cybersecurity professionals alike must stay informed and prepared to navigate this rapidly changing digital frontier.
- As these platforms grow more secure, decentralized, and integrated into broader digital ecosystems, their influence expands.
- A VPN encrypts the data traffic and keeps your activities private on the dark web.
- In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet.
- As home to marketplaces that sell items like illegal drugs and firearms, the Dark Web can be extremely dangerous.

It is one of the most active and up to date markets and always provides new and updated malware and data. Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience.
Typical Use-Cases Of Dark-Web Marketplaces In 2025

All the payments were made through cryptocurrency, further enhancing marketplace anonymity. The users on this site can review and rate the products that promote reliable and fraudster vendors. Nemesis Market is a relatively new wallet-less shop on dark web where you don’t need to deposit any amount in your wallet before buying products from here. The platform allows buyers to review the vendor’s products and services, so it’s easy for them to decide if the vendor is reputable or just scamming them.
One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. Payments on the platform were made exclusively with Monero, a privacy-enhanced cryptocurrency the architecture of which makes tracing blockchain transactions much more of a pain for authorities. Launched in 2020, Archetyp was Europe’s longest-serving drug market at the time of its takedown last week, and authorities today confirmed a number of key arrests. When your data is found on the dark web, it means that you’ve been compromised. Therefore, you need to start by changing your passwords, and you need to notify your credit card or bank provider.
- It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security.
- It’ll make it very interesting, looking into 2025, when we start thinking about predictions in terms of what that will look like, but hopefully that answers your question.
- If you’re into a darknet market that feels cutting-edge and keeps your coins safe, ASAP Darknet Market’s a gem—just don’t expect a massive catalog yet; it’s more about precision than sprawl.
- Torzon market made its debut in September 2022, and ever since, it has been on an upward trajectory.
- Ransomware gangs are also expected to diversify their tactics, targeting smaller companies and individual users to maximize their reach.
- According to Forbes, by 2025, damage related to cyber attacks is projected to reach $10.5 trillion annually.
Drawing on industry expertise, this post identifies seven major threats and trends expected to shape the darknet in the coming year. The dark web continues to pose a significant risk to businesses, facilitating cybercriminal activities that exploit sensitive data and security weaknesses. Without proactive defenses, companies face financial losses, reputational damage, and regulatory consequences. Conducting a cybersecurity assessment and implementing dark web monitoring are essential steps in mitigating these threats. Cybernod provides cutting-edge security solutions, helping businesses detect exposed credentials, security vulnerabilities, and cyber threats before they escalate. Protect your organization today—schedule a dark web risk assessment with Cybernod.
Dark web hackers often use botnets to carry out DDoS attacks, causing disruption and financial loss for their targets. Social engineering remains a significant threat in the cyber landscape, and we expect to see more sophisticated tactics in 2025. Criminals will increasingly exploit psychological manipulation to deceive victims, using advanced techniques that involve personalized and context-aware phishing schemes. Additionally, threat actors appear to be increasingly using multiple programming languages.
We are not responsible for any harm or loss you may receive by following links listed on this site. mark it means it has been verified as a scam service and it should be avoided. Securily offers the ultimate solution for small to medium-sized businesses, blending cutting-edge AI with expert human insight to deliver the world’s easiest and most effective pentesting experience. Pluribus One develops customized solutions and other data-driven applications to secure your business and your devices.|Features like multi-signature wallets, end-to-end encrypted messaging, and decentralized hosting environments reduce the risk of detection. Many vendors rotate addresses and aliases regularly to avoid tracking and maintain anonymity. Darknet marketplaces remain central to illicit trade in 2025, with evolving business models, payment systems, and law enforcement responses. This survey highlights active and recently shuttered markets with actionable metrics and intelligence for threat hunters, CISOs, and red team leaders. As the world navigated an evolving cybersecurity landscape in 2024, trends in malware, ransomware, and dark web activities highlighted the increasing sophistication of cybercriminal tactics. BriansClub is also one of the largest dark web marketplaces that is also available on the clear web.|A report by Chainalysis indicated that more than 40% of cryptocurrency transactions on the darknet involve privacy coins, highlighting their growing popularity among criminals. So if we look at some of the really big names that took a hit year, two that spring to mind is obviously LockBit and then BlackCat. BlackCat, kind of, got forgotten about because it happened quite early in the year and went out with a whimper rather than a bang. But I think that one is especially indicative of how smaller-, not actors that are calling the shots but maybe affiliates of ransomware gangs can get burned as a result of law enforcement disruption. The surface you see with search engines like Google is the “clearnet,” but a much larger portion lurks beneath the water – the deep web.}