Since these pages would otherwise be behind paywalls, it stands to reason that this would go against copyright laws. The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Proton also offers other security tools besides ProtonMail, such as Proton Drive, Proton Pass, Proton Calendar, and Proton VPN.
Tor Crypto Wallets

Unlike the regular internet, the Tor network can’t be accessed via standard browsers. The Internet is a vast and complex landscape, much larger than the familiar interface we use every day. With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management. It is designed to ensure user anonymity while offering access to a diverse array of information available on the dark web.
How To Protect Your Identity While Browsing The Dark Web
- Tor uses multi-layered encryption and routes data through multiple relays (entry, middle, and exit nodes), which increases latency to enhance anonymity.
- Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
- Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info.
- In order to avoid censorship of their content, they’ve created a .onion site to ensure it’s accessible for all.
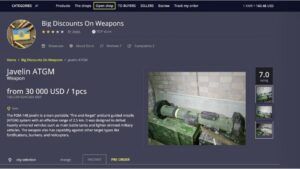
- Its 14,000+ users and 1,000+ vendors leverage multi-crypto flexibility for seamless darknet trading.
Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. It allows you to search for images, maps, files, videos, social media posts, and more. It may initially look abandoned, but the community members will answer your questions.

CORE PROTECTION
It works by starting servers locally on your computer that are then shared with others as Tor services. However, it works best in real-time since the file transfers are interrupted if you turn off your system. SecureDrop allows whistleblowers to establish encrypted communication with a news outlet. It’s used by 50+ news organizations, including The New York Times, The Washington Post, The Intercept, The Globe and Mail, ProPublica, and more.
But because it’s not regulated, it’s also a potentially attractive place for cybercriminals to hang out. That’s why it’s important to be extra careful when browsing the dark web—sites you can find there may host sensitive content, foster illegal activity, or pose security threats. However, there are steps you can take to stay safer on the dark web, including never sharing personal info, using a VPN, and installing antivirus software. You might have arrived here through Google, but you’ll be hard pressed to use Google to get to the dark web.
Top 10 Best Dark Web Search Engines In 2025 Safe & Anonymous Browsing Tools For Tor Users
However, to maintain the servers, they offer the possibility of inserting advertising banners on their home page. The dark web in 2025 still holds power, but only for users who browse smartly. Stick to verified directories, question everything, and always put your privacy first.
Avoid Sharing Personal Information
Let’s unravel the mysteries of the dark web, from its safest havens to the threats lurking in its shadows. Ahmia developers believe that the Tor network is an important distributed platform to protect anonymity and privacy around the world. While its name may indicate danger, the dark web can actually be a safe place. It provides safety and anonymity for journalists, privacy-conscious users, or those in high-censorship countries.
Hidden Wiki
Beyond its directory functions, the platform also serves as a community hub where you can discuss various topics and share your experiences. Its longevity and reputation have solidified its position as a cornerstone of the Dark Web community. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online.
Protect Yourself
- At Proton, Douglas continues to explore his passion for privacy and all things VPN.
- As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms.
- However, over the years, the Hidden Wiki name has become controversial.
- Its 10,000+ users and 800+ vendors rely on 2FA and escrow security for private cryptocurrency trading.
- It provides safety and anonymity for journalists, privacy-conscious users, or those in high-censorship countries.
My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy.

What Are Onion Sites And Dark Web Websites?
However, the technology that Yippy manages, was created in Carnegie Mellon. In addition, this included the acquisition of an unlimited license for the software known as Vivisimo’s Velocity, acquired by IBM in 2012 and renamed IBM Watson Explorer. Founded in 1998 as Ixquick.com, we later changed the name to Startpage.com. “If you’re completely new, start with this Hidden Wiki beginner’s guide to understand how it works before browsing. Caution, verification, and patience are your best defenses when navigating the dark web safely.
What Is The Dark Web And How To Access It?
To conclude, you may also find the links of other dark web search engines but these happen to be the ones that stand out the most. This particular search engine was built by Hugbunt3r, a prominent member of the popular Dread service on the dark web. It aims to serve as a database through which users can search for products from different vendors in different marketplaces on the dark web. The Hidden Wiki is a dark web directory that can only be accessed using the Tor network. The Hidden Wiki is a valuable resource for those who wish to explore the dark web, as it provides a safe and easy way to access a variety of different sites.
Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage. This isolates any potential malware and prevents cross-contamination with your personal data. Using Tails OS can further security, as all your data is reset every time you close the device. Many free VPN providers lack basic security features and track your online activity, so they don’t offer much privacy. That’s why it’s important to verify links through trusted directories and proceed with caution. While the best dark web sites listed above are a good starting point for a safe, legal surfing experience on Tor, there really is no substitute for a VPN.

It is an archive stored on the Dark Web that keeps a snapshot of websites on the surface internet. The useful site allows you to see how a website looked at an earlier date. This lets you check what information it contained at a previous point in time.
Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.
The darknet, also known as the dark web, is a hidden part of the internet that cannot be accessed via normal search engines such as Google or Bing…. From drug trafficking to arms deals to stolen data, the dark web provides a marketplace for many illegal goods and services. This has led to a negative reputation and is attracting the attention of law enforcement agencies.