Torrez has been steady since 2020, rocking 4,650+ listings with BTC, LTC, ZCash, and Monero. Wallet-less payments and multi-signature deals make it a safe bet—I’ve never worried about getting burned, even after a close call with a dodgy vendor once. It’s all about drugs and digital goodies, with BTC and Monero on deck. Quality beats quantity here—their listings aren’t massive, but they’re solid. The site looks sharp, and vendor profiles are packed with ratings and reviews. They’ve got forums where people actually talk, which builds trust—kinda like the Telegram vibe.
Making Cybercrime Easy For Anyone
Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. For example, it maintains your privacy and enables you to access untraceable content and services. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. With the onion browser, you can access ordinary HTTPS websites on the web.
The forum features a selective membership process, which has earned it a reputation as the best place for seasoned hackers where they can easily exchange knowledge. Besides, its expertise database expands constantly and covers hacking methods and tools that threat actors can use. It has a huge and active user base as well as a marketplace that makes trading of hacked credentials and stolen data seamless.

While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security. ProPublica is an investigative news site owned by an independent nonprofit that exposes abuses of power and corruption. It hosts an onion site so people in countries with restricted press freedom can access its journalism, which covers everything from hacktivism to government repression. The dark web, on the other hand, is a small part of the deep web that requires special tools like the Tor browser to access. Ransomware gangs are also expected to diversify their tactics, targeting smaller companies and individual users to maximize their reach. Businesses should prepare for more sophisticated ransomware campaigns, potentially leveraging AI to exploit security gaps.
Topics And Products Sold
You can use dark web monitoring tools, such as NordVPN’s Dark Web Monitor, to check if your data has been leaked. These tools scan dark web forums and marketplaces for any signs of your compromised credentials. There is no need to visit darknet marketplaces yourself to know whether your data was leaked. Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services. They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity.
Tor2(Run Out The Back)Door: Exit Scam Or Seizure?
This marketplace accepts payments via Monero but also supports the Escrow system. DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users. It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services. The marketplace is much more organized, which makes it easy to use and navigate. Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce. It offers a wide range of goods and services with robust anti-DDoS protection (with military-grade security protocols) and no JavaScript, ensuring privacy and uptime.
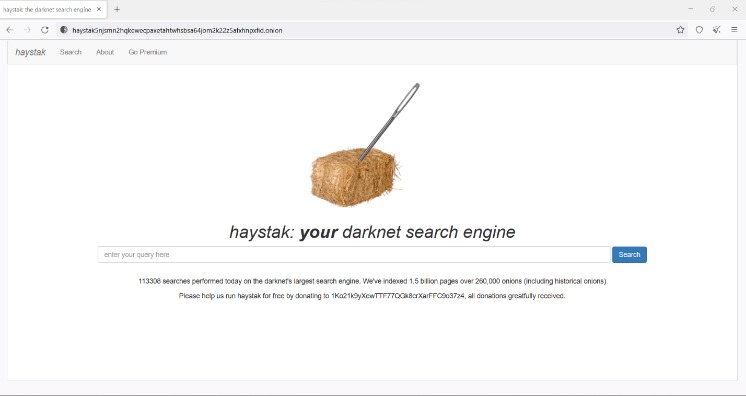
How Do I Verify Onion Links?
Nevertheless, the digital landscape is under constant cyber threat, and individual or business data can find its way onto the dark web. Therefore, it’s a no-brainer that businesses should implement dark web monitoring to identify data breaches, cyber risks, and several other illegal activities. That way, a business can stay ahead of the game and respond swiftly to any possible threat, while protecting its reputation and customers. Tor offers secure and encrypted access to the dark web forums, ensuring that the user’s IP address is hidden and difficult to trace.
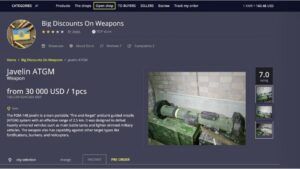
- In many countries, strict laws limit who can legally buy, own, or carry firearms.
- With fast order processing, product reviews, and secure payments, it’s a trusted platform for cannabis enthusiasts in the darknet space.
- For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions.
- Over the years, numerous successful operations have been conducted, resulting in the takedown of dark web marketplaces and the arrest of their operators.
- Believe it or not, some dark web marketplaces have pretty advanced systems for building trust.
Is Accessing The Dark Web Illegal?
While it can be used for illegal activities, there are also perfectly legitimate forums, social networks, and communities. The dark web market hosts a variety of cybercriminal groups, ranging from state-sponsored actors to independent ransomware gangs. These groups operate globally, leveraging sophisticated tools and networks to execute large-scale attacks and maintain anonymity.
It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting. A Canadian market established in 2021, WTN offers over 9,000 products, including narcotics, fake goods, and digital services. It operates in both French and English and has built a reputation for ease-of-use. This article reveals the top 10 dark web markets dominating in 2025, their unique characteristics, and the critical implications for enterprise cybersecurity. Russian Market has consistently remained one of the most popular and valuable data stores on the dark web. Its affordability and reliability have earned it a loyal customer base.
What’s The Difference Between The Deep Web Vs Dark Web?
For example, YoMix is a bitcoin mixer used by the Lazarus Group to launder their stolen cryptocurrency profits, with a massive influx of laundered funds in 2023. Crypto-laundering threat actors specialize in stealing and hiding the origins of their cryptocurrency. Cryptojacking involves secretly mining for cryptocurrency via the victim’s device. The proliferation of IoT and 5G devices will provide new attack vectors for infostealer gangs. As AI becomes more accessible, hackers may use AI-driven tools to automate data theft on a massive scale. A brief timeline of darknet market evolution leading to 2025’s top players.

It’s recommended not to use new alternative links as they could just be planned exit scams. Moreover, the layers of encryption and the bounce of your data from node to node effectively mask your IP address, enabling online anonymity. It allows access to the .onion sites on the dark web that you won’t find using a regular browser.
Dark Web Beginners To Advanced Access Tools Complete Bible 100
It’s made up of forums, marketplaces, and websites you can’t find with a Google search and requires specialized software to access, such as the Tor Browser. The forums function as secret darknet markets (most of the time) where criminals and hackers sell stolen goods. They enjoy the fact that these forums are buried in hard-to-find locations that are difficult to detect. In 2025, top darknet marketplaces continue to operate, though their environment has become more volatile. Buyers can enable two-factor authentication, and transactions are protected by escrow, including multisignature escrow for added safety. Vendors must post bonds to discourage scams, and the market maintains an active dispute resolution system.

Unlike traditional TLDs, servers using the onion TLD are more difficult to locate. This makes it more difficult for authorities to locate and take down these sites. Exploring the dark web can be eye-opening, but it’s also risky without the right protection.