
The dark web is often misunderstood due to the illegal activities that occur within its depths. However, it’s important to note that not everything on the dark web is illegal. Journalists, activists, and individuals concerned about privacy and censorship often use the dark web to communicate securely and anonymously. Nevertheless, caution should always be exercised when venturing into this hidden realm.
What Is The Dark Web, And Is It Illegal To Access?
That’s why I’m not going to provide links or detailed instructions for accessing the internet’s shadier side. Cryptocurrency activities, discussions and communities, and even academic resources further populate this hidden corner of the internet. However, it is crucial to recognize the dual nature of the Dark Web, understanding that while it has legitimate uses, it also harbors risks and associations with unlawful activities. Users navigating this space should exercise caution and be aware of the potential legal consequences tied to specific content and transactions. Unlike the surface web, which can be indexed by standard search engines, the dark web exists on encrypted networks and hosts websites with random, complex URLs. This layered encryption and anonymization make it difficult for authorities or outsiders to trace activities or identify participants.

Top 10 Best Dark Web Search Engines In 2025 Safe &
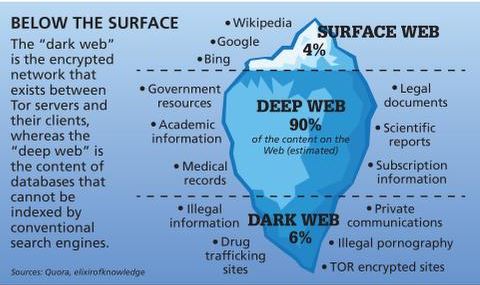
Deep web content includes academic research papers, court documents, or medical records. For example, when you sign in to your healthcare provider’s portal to view test results or request prescription refills, you’re accessing the deep web. Furthermore, the dark web’s reputation often attracts curious individuals who are unaware of the potential risks. Casual exploration can lead to exposure to malware, scams, or illegal content, any of which could have severe consequences, both digitally and legally. However, engaging in illegal activities on the dark web is against the law. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser.
Table Of Contents
The developers of the Tor Browser regularly release updates that contain security patches and improvements. Configure the Tor Browser to check for updates automatically or periodically visit the official Tor Project website to download the latest version. Once the Tor Browser is launched, it may take a few moments to connect to the Tor network. During this process, various nodes are selected, and encryption keys are exchanged to ensure a secure connection.
ExpressVPN is slightly expensive but a trustworthy provider for risk-free dark web browsing. You’ll also enjoy its Smart DNS support, 24/7 live chat service, the Keys password manager, and a lot more. Feel free to grab its 49% discount thanks to 3 free months for the annual plan. This provider’s performance is top-tier, with full Tor Over VPN support to make things simpler. ExpressVPN’s intuitive apps work on up to 8 devices at a time, ensuring protection for the entire family.

Ensuring Security And Anonymity

These computers are all owned by volunteers, passionate about privacy and happy to offer up their device to help others. Traffic is relayed through three nodes each time it passes through the Tor network. Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers. The dark web is a small, hidden subset of the deep web that requires special tools to access.
- If you value a speedy browsing experience, chances are Tor won’t be your browser of choice.
- I also worked at CNN International, where I did field producing and reporting on sports that are popular with worldwide audiences.
- In some parts of the world, simply using a browser like Tor can get you flagged by these agencies, even if you don’t partake in illegal activity.
- You may encounter fake marketplaces promising illicit goods or services but delivering nothing after payment.
- When using the Tor Browser, it’s crucial to maintain and respect the privacy settings.
However, the Dark Web is the most hidden and secretive layer of the Deep Web. It requires specialized software to access and is intentionally kept anonymous and out of reach of mainstream search engines. The Dark Web—a hidden part of the internet accessible only through specialized tools like Tor—often conjures images of mystery, intrigue, and even danger. However, navigating this hidden digital landscape in 2025 presents heightened security risks, from advanced cyber threats to targeted surveillance. This guide provides clear, step-by-step instructions to safely explore the Dark Web using Tor, helping you stay protected, informed, and anonymous. Despite the dark web’s anonymity, users still need tools to navigate its vast and often confusing landscape.
It allows users to explore hidden marketplaces, access encrypted messaging services, and browse content that may not be available through traditional means. In this article, we discussed the background of the Dark Web and its association with both legal and illegal activities. It’s important to note that not everything on the Dark Web is illegal. Whistleblowers, for example, may use the Dark Web to anonymously share sensitive information with journalists or law enforcement agencies. Moreover, there are legitimate websites and forums that discuss topics such as privacy, cybersecurity, and digital rights. The privacy offered by the Tor browser is important in the current digital age.
Whistleblowing And Anonymous Information Sharing
The quickest way to access the dark web is to download and install Tor Browser, which will route your traffic through the Tor network and let you access the dark web. On Tor, you can type in any URL you’d like to visit, including .onion links on the dark web. However, it is equally important to be aware of the illegal activities that take place on the Dark Web. These activities can range from the sale of illegal drugs, weapons, and counterfeit goods to human trafficking and hacking services. Engaging in or supporting these illegal activities is not only unethical but also carries significant legal consequences. When navigating the Dark Web, it is crucial to take steps to protect your personal information.
- The Dark Web can provide a platform for individuals to share information, documents, or evidence anonymously, ensuring protection against potential retaliation.
- When accessing the Dark Web, you will encounter websites with addresses that end in “.onion”.
- My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.
- Webpages on the open web will show up in search results on sites like Google and Bing.
Illegal Trade And Services
Browsers with the appropriate proxy can reach these sites, but others can’t. While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider. Accessing the dark web is legal in India as long as you do not engage in illegal activities such as buying drugs or hacking services.
To understand how this is possible, we need to see how the web has many layers, and not all content is publicly available from a search engine query. In this guide, we’ll explain what the dark web is, how to access it safely, and why using a VPN (Virtual Private Network) with Tor is essential for anonymity. That’s a trick question, because there isn’t even a good free VPN, much less a best VPN. Freebie VPNs will track their users’ online usage, as they make money by selling this tracking info to advertisers and other nosy parties. We’ve found that Tor is an excellent way to keep your internet browser-based online activities undercover, although we’ve also seen how using the Tor Browser can bring unwanted attention.
Only click on trusted links and download files from reputable sources. Where possible, enable two-factor authentication for your Dark Web accounts. This adds an extra layer of security by requiring a second form of authentication, such as a unique code sent to your mobile device, in addition to your password. Minimize the use of your real name, address, phone number, or any other personally identifiable information. Adopt a pseudonym or anonymous username to help protect your identity. Stay informed about the latest security practices and developments related to the Dark Web.
Step 2: Navigating Safely
The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web. No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web. While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions. Avoid downloading files from unknown sources while browsing the Dark Web.
It also introduced a bug bounty program, hired a cybersecurity consulting firm to test its infrastructure, and then carried out a third-party security audit. NordVPN has a huge worldwide network of RAM-only servers and high standards of both privacy and security. It makes visiting the dark web easy, with dedicated Onion Over VPN servers that connect you to the Tor network via the VPN. This negates the need to download, install, and run the Tor browser separately, and lets you access the Tor network without your ISP knowing. The most common way to safely access the dark web is by connecting to a VPN and then opening the Tor browser. For anyone considering exploring the Dark Web, it’s crucial to tread with caution.



