
This, joined by incredible value and the price of around $2/mo, makes PIA very attractive. Unfortunately, it’s slower than NordVPN and ExpressVPN but overall, its performance is admirable in practice. ExpressVPN is slightly expensive but a trustworthy provider for risk-free dark web browsing.
Changing any of the default settings can make websites misbehave or not load correctly. While Bitcoin and other cryptocurrencies provide some level of anonymity, blockchain analysis tools can trace illicit transactions. One of the darkest aspects of the dark web involves human trafficking, illegal pornography, and other forms of exploitation. Hacked data, credit card details, and personal information are frequently traded on the dark web.
Is Accessing The Dark Web Illegal?
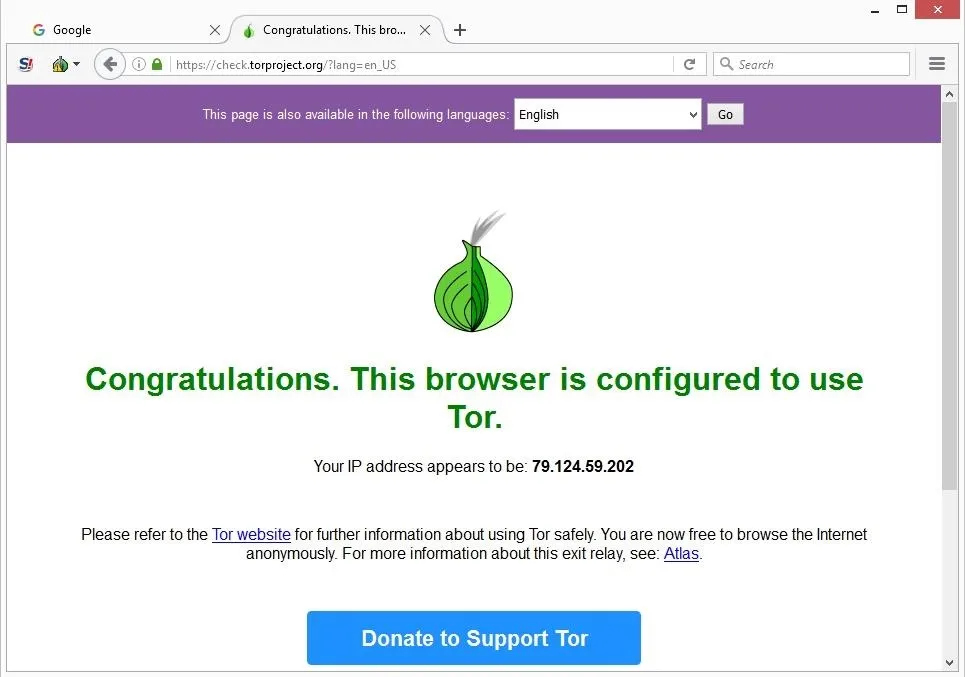
That said, there are still some ways to protect yourself when using the Tor Browser. The dark web refers to websites that are not indexed by traditional search engines like Google or Bing. These sites exist on darknets which require specialized software to access. The dark web is a hidden part of the internet not indexed by regular search engines, accessed through specialized browsers like Tor. It hosts both legal and illegal activities, offering anonymity but also posing risks like scams and illicit content. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web.
Wrap-Up: Staying Safe While Accessing The Dark Web
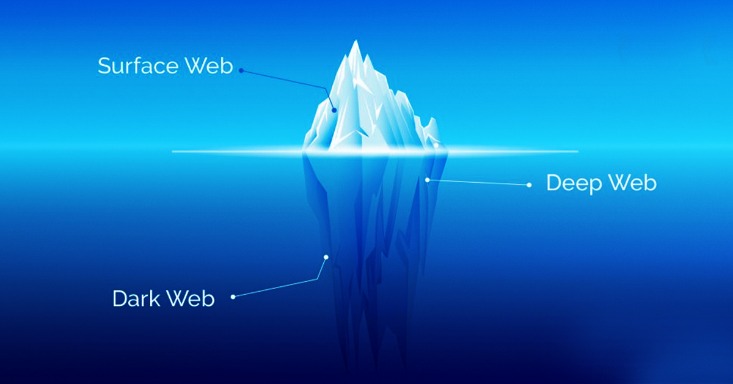
It’s a less recommended configuration, though it does offer protection against exit nodes run by those with malicious intent. The deep web refers to any web content that is not indexed or pages that can’t be found with a search engine. Examples of the deep web include any websites that are behind a paywall or require login credentials. Most internet users access the deep web several times a day to perform common tasks, such as checking email, accessing a bank account, or reviewing health or school records.
Tor Over VPN servers are identified with an onion symbol and found in the country list. In addition, even if the Tor node fails, your data won’t be exposed because the VPN’s encryption still holds up. As mentioned, we recommend using a safe provider like NordVPN, which also offers Onion Over VPN servers perfect for accessing the dark web safely. The dark web is a hidden part of the internet that requires tools like Tor to access. While it offers privacy and anonymity, it also comes with risks. To protect your security, always use a VPN like NymVPN, disable tracking features, and follow safe browsing practices.

Top 10 Best Dark Web Search Engines In 2025 Safe &
Always stick to legal use, and don’t click random links without protection. To access the dark web safely, it’s necessary to use a dark web browser like Tor in combination with trusted dark web directories and search engines to help you find reliable sites. You should also make sure your device is protected by strong antivirus software, and consider using a VPN to mask your activity on the dark web. The most common tool for accessing the Dark Web is Tor (The Onion Router). Tor provides anonymity through a process known as “onion routing,” where internet traffic is encrypted and passed through multiple network nodes.
- A VPN is a confusing factor for many because there are two ways to use it with Tor.
- Click the button, get the provider for around $3.3/mo, and install it on your device.
- Plus, there are only a few VPN providers that offer this option (PrivateVPN is the only one that comes to mind).
- Setting up NordVPN will ensure that it encrypts your connection, so your ISP cannot see that you are using Tor.
- With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential.
More Computing Guides

Speeds were solid for browsing text-heavy dark websites and small links. There were no random crashes or aggressive throttling halfway through a session. We got consistent performance on European and US free servers, and Tor connections stayed stable even when flipping between sites. It’s not as fast as NordVPN or Proton VPN, but for free access, it was smoother than expected — especially compared to some “free forever” VPNs that are borderline unusable. If you want a free VPN that’s low-key but still packs serious stealth, Hide.me is one of the best free VPNs we tested to access the dark web safely. It’s lightweight, privacy-focused, and gives you more flexibility than most other free options, without sacrificing speed or leaking your data.
Practice safe, smart digital habits if you must use Tor to log into personal accounts. For instance, always use strong passwords that mix letters and symbols, making them hard to guess. Use different passwords for each account so that a single compromised account doesn’t affect others. Though secure against everyday threats, Tor is vulnerable to targeted attacks from state-level actors. A VPN app opens another potential vulnerability, as it can log the sites you visit via Tor.
Don’t Use Your Main Device
You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. You can also use it if you don’t want your network administrator or ISP to be aware of your Tor usage. However, if you don’t fall into these categories, or are a high-risk internet user (e.g., an investigative journalist or whistleblower), combining a VPN with Tor might be unnecessary. This provider’s performance is top-tier, with full Tor Over VPN support to make things simpler. Connect to ANY of its 3,000+ servers, open Tor, and do your magic!
Connect To The Tor Network
Whether you’re exploring it out of curiosity or for legitimate personal reasons, it’s essential to approach this hidden realm with the right knowledge, tools, and security measures. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. Tor Browser is the most popular option for accessing the dark web, known for its strong privacy and anonymity features.
That said, a significant chunk of U.S.-based activity on the dark web still revolves around illegal marketplaces—selling things like stolen data, counterfeit documents, and even drugs. Look for features like real-time alerting, coverage of multiple dark web forums and marketplaces, credential and data leak detection, and integration with your existing security stack. Strong vendor support, customizable alerts, and compliance alignment are also key to ensuring the tool delivers actionable insights, rather than just noise. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace. These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network. These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold.
Just like invasions of search engines have helped us to acquire the required info; in the same way, … However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups. Illegal marketplaces are merely a small fraction of what’s actually there. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor).
The dark web is also unregulated, meaning that it is run and upheld by a vast network of individuals around the world. This network contains thousands of volunteers who operate proxy servers to route dark web requests. As such, no one is responsible for setting rules or ensuring their adherence. This operating model is what makes the dark web such a valuable and appealing tool for cybercriminals and other people with questionable intentions.
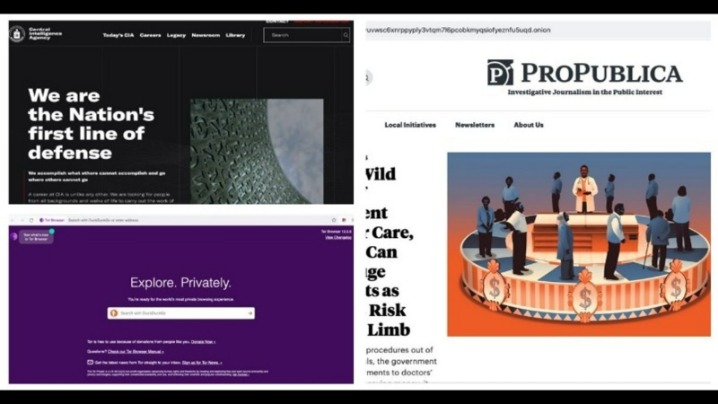
In fact, create new throwaway accounts and documents if possible. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Avoid using payment methods that can easily expose your identity. We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Many services that are allegedly offered on the dark web are scams.
Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether. The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. Contrary to a widespread misconception, the dark web is a tiny part of the web. According to Recorded Future research1, out of 55,000 onion domains discovered, only 8,400 have a live site.



