Hence, it’s advisable not to download files via Tor, especially from unknown sources. The last node (exit node), through which Tor routes your traffic, is delicate. In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts. Whenever you enter any domain into the address bar, your browser uses HTTP to find and request the data from the relevant server.
Don’t Provide Personal Information
- Malicious actors can prey on unsuspecting users without leaving much of a digital footprint on Tor, so it’s often just a matter of time before you run into one.
- Please check your local laws to ensure your use of VPN complies with statutory requirements.
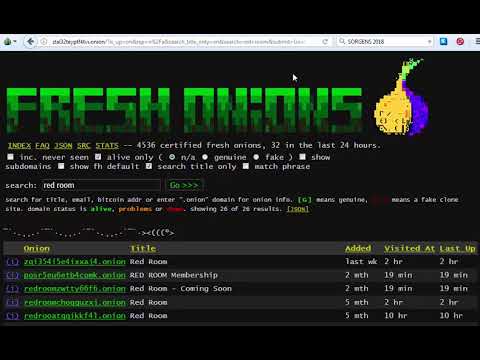
- Finding data on the dark web can be challenging, in this post we’ll cover how the dark web works, how to access it, and the top 5 dark web search engines.
- For example, connecting to Facebook’s regular site over Tor is known to be problematic – the unusual IP addresses Tor chooses as your exit nodes can make you appear like a bot.
- The dark web is a part of the deep web that contains websites not included in the mainstream search engine index.
- In addition, Haystak offers a premium plan that allows deeper search, email alerts, and access to historical content.
You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. SecureDrop is a dark web link that allows whistleblowers on the dark web to communicate and share information with journalists safely and without being tracked. The social media giant is also aware of the many attempts by repressive regimes to restrict its access.
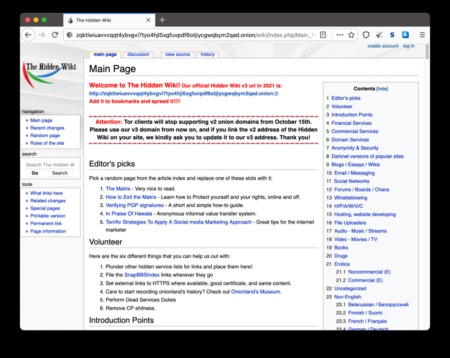
Dark Web Links: The Best onion And Tor Sites In 2025
These attacks overwhelm servers by flooding them with massive amounts of fake traffic, making legitimate access nearly impossible. Since many dark web platforms lack the sophisticated resources needed to defend against such large-scale disruptions, affected .onion sites can remain offline for extended periods. Still, since they exist within the dark web, there is a high chance that malicious entities have co-opted one or more for illegal activities. Thus, staying connected to a VPN when you access these sites is vital.
Use it to search the normal internet from the privacy of your Tor Browser. Torch is one of the oldest and most popular onion search engines on the dark web, serving over 80,000 requests per day. Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins. Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. It is easily accessible by the general public and requires no special configuration. You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome.
There are several programs that hackers frequently use on the dark web. Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store.
Pro Tip: Use A VPN To Stay Safe When Using The Dark Web Search Engines

Also, you must log in or have a specific IP address or URL to access the deep web content. NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web.

First, Install A Reliable VPN
If you need to access dark web resources, these are the steps you need to take. The dark web, however, requires special software to access, as explained below. Here’s everything you need to know about this other internet, as well as how to access it. The area of the internet we access daily is known as the clear or surface web.
Can Malware Be Present On The Dark Web?
The name “onion” comes from the layered structure of the encryption, similar to the layers of an onion. These websites are not accessible via normal web browsers, but require special software such as the Tor browser. Keybase is an encrypted communication platform that enables secure file-sharing and messaging using public key cryptography. Though not specifically a .onion service, Keybase integrates well with privacy-focused ecosystems like Tor.
Separate Your Real Life From Your Online Persona
Darknet markets facilitate transactions for illegal goods and services. Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. While many dark marketplaces have been shut down by authorities, new ones soon appear in their place. Be mindful that not all content on the dark web is legal or safe; avoid engaging with illicit activities or sites promoting harmful behavior.
Risks And Challenges Associated With Onion Sites
Ahmia has become a trusted tool for navigating the Dark Web, with thousands of users relying on it for its transparency and user-reporting features. To safely use the Hidden Wiki, verifying the authenticity of links is essential. First, rely on community-vetted sources and updated link lists from trusted forums like Dread or The Hub, where users report scams and share verified onion addresses. Check for recent user reviews or feedback to ensure the site is still operational and legitimate.
While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider. This blog offers a complete guide on how to access the Dark Web using the Tor Browser, along with step-by-step instructions, security tips, legal warnings, and real-world examples. Stay informed about the latest darknet marketplaces, secure browsing practices, and privacy tools.
Scroll on to learn more about dark web links (also called Tor links or onion sites), get the right links for some of the best Tor sites, and find out how to visit them safely. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
{While exploring the dark web can offer valuable privacy benefits, it’s crucial to understand common risks and how to manage them effectively. } mark it means it has been verified as a scam service and it should be avoided. Ahmia promotes transparency by being open-source and allowing contributions. Its operations focus on respecting user privacy and maintaining anonymity through the use of the Tor network.|SecureDrop’s .onion link is a platform designed for whistleblowers to securely and anonymously submit sensitive information to journalists. Used by over 70 media organizations worldwide, it supports encrypted communication and protects the identities of both sources and reporters. SecureDrop is maintained by the Freedom of the Press Foundation and is a trusted tool for investigative reporting in high-risk environments. Bearing in mind all the dangers, if you’re sure you’re willing to accept the risks, all you need to enter the dark web and access onion sites is an internet connection and Tor Browser software. Onion sites are dark web sites that can only be reached through online routing via Tor, in which encrypted data passes through multiple nodes before reaching its destination.|It publishes news in English and other major languages like Italian and Spanish. The dark web version of Facebook isn’t malicious, but if you log into it, it will keep your data. The advantage of this version is that you can effectively create a Facebook account anonymously or use this social media platform in a restricted region. Consequently, you’ll have maximum privacy while sharing opinions and anti-oppression resources. If we need a website to get links to other hidden sites, we will choose Hidden Wiki. But if you are thinking you can find links to the deepest part of the dark web using this site, it’s not that simple.|Avoid downloading files or opening attachments from unknown sources, as these can contain malware. Use strong, unique passwords and enable two-factor authentication where possible. While it’s not 100% foolproof (no directory is), the Hidden Wiki helps minimize risks and provides a safer entry point for users who are new to the Tor network.|You’ll get unbiased, organic search results without getting any of your browsing behavior logged. Using DuckDuckGo over Tor will also let you see onion sites and normal pages in your search results. Discover how to safely navigate dark web onion sites while ensuring your privacy and security online. Dark web links are unique .onion URLs that grant access to hidden websites on the dark web, which can only be reached using the Tor browser for privacy and anonymity. AVG Secure VPN encrypts your internet traffic and obscures your IP address every time you use it to go online — dark web or not. With a variety of server locations around the world to choose from, you’ll be able to navigate the web more privately and access the content you want.}
What Is The Hidden Wiki Used For?
However, time has changed, and now several services offer free dark web access with the least amount of technical knowledge. SecureDrop is one of the most reliable file-sharing sites on the deep web. SecureDrop helps whistleblowers anonymously send sensitive material to media outlets via a unique SecureDrop URL. The files are automatically encrypted, and the sender’s IP is not logged. At this level, all features from the Tor Browser and other websites are enabled.



