The dark web is a hidden part of the internet that stays out of reach for normal browsers and search engines. Unlike the websites you find on Google, the dark web uses special encryption and requires unique browsers like Tor to open its pages. Surfing it to commit illegal acts such as purchasing contraband or selling stolen data, however, is illegal and subject to law enforcement. The history of the Dark Web as a hidden network is tightly connected with the history of anonymous technologies and encryption.
If you’re browsing a site with a “.onion” domain, you are on a hidden network. These addresses are designed for the Tor browser, the most common tool for accessing it. Regular browsers like Chrome or Firefox cannot reach these sites, so you’ll need a specialized browser — and it’s impossible to access them by accident.
- Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity.
- Your online activity and communications remain private and secret on the dark web.
- While many sites offer valuable services, others may host illegal activities or harmful content.
- Look no further if you want good music while navigating the dark web.
- You should never trust websites and forums on the dark web with your personal information.
Importantly, not all users of these spaces are criminals—some are security professionals, journalists, or researchers trying to understand threat actors or investigate breaches. The dark web is a hidden segment of the internet that isn’t indexed by standard search engines. It lives inside encrypted networks like Tor and I2P, allowing users and site operators to remain anonymous. The dark web refers to a concealed part of the internet that cannot be accessed through standard web browsers like Chrome or Safari. Instead, it requires specialized software such as the Tor browser, which anonymizes user activity by routing traffic through multiple encrypted nodes. This layer of the internet is purpose-built to provide privacy, ensuring users can browse or host websites without revealing their identities or locations.

Dark Web Phishing Kits: How Hackers Sell Ready-Made Scams

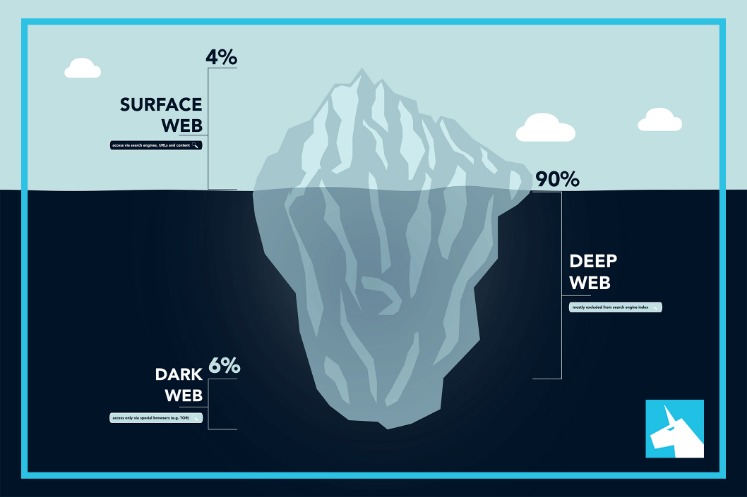
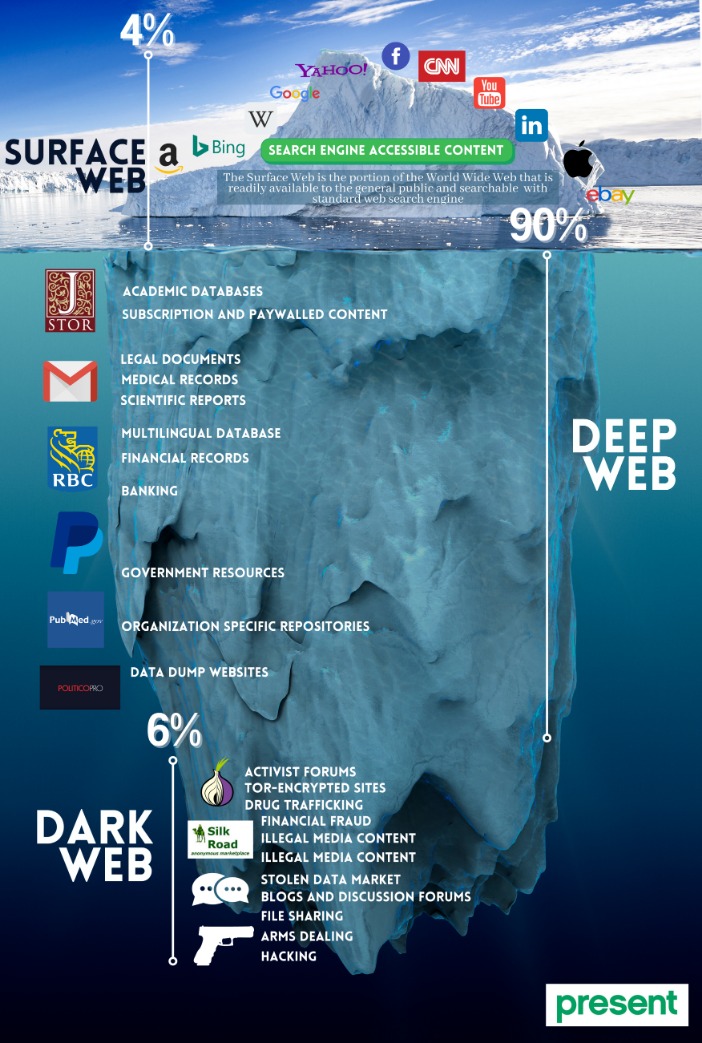
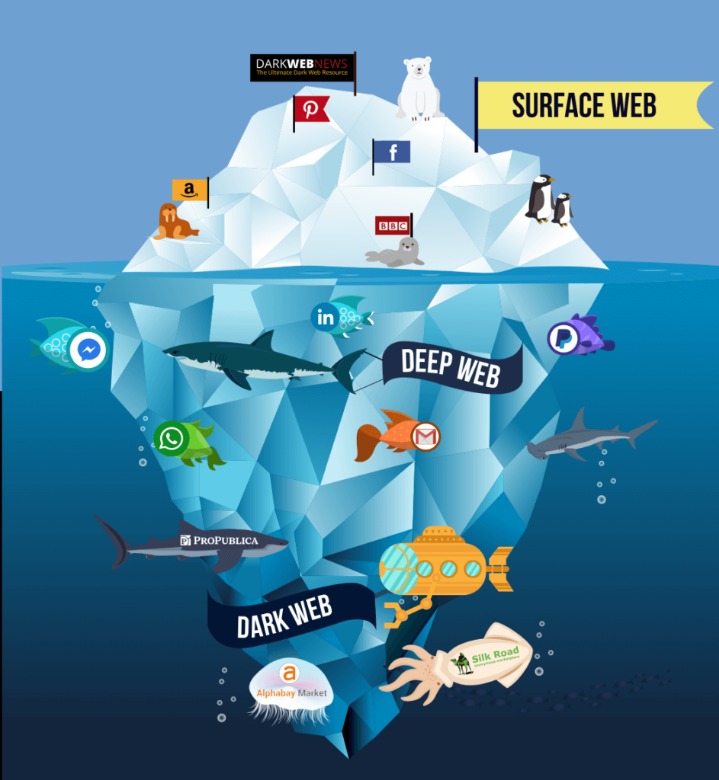
Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online. Even if users maintain their anonymity, they are not immune from detection. The Dark Web refers to a specific section of the internet that exists on an encrypted network, intentionally hidden and accessible only through specialized software. It forms a small part of the Deep Web, a term that encompasses all parts of the internet that are not indexed by traditional search engines.
Should You Use A VPN And Tor?
A VPN will mask your location and stop the online breadcrumbs that can lead back to you. Connections made while a VPN is active will also be encrypted, helping you stay protected from eavesdropping and man-in-the-middle attacks. You can usually select the location you want to appear to originate from and VPNs will use a collection of servers and relays to make tracing your IP difficult. First — and this is strongly recommended — you should install a Virtual Private Network (VPN).
Take Extra Security Precautions
Some users also share links on encrypted apps like Telegram or Keybase that you can check. Blockchain even has an HTTPS security certificate for even better protection. Unlike other search engines, it does not collect or share web activities and personal data of users.
How Do You Get On The Dark Web?
Once you step inside the dark web, you’ll find a hidden network where stolen data changes hands every day. Cybercriminals use it to trade Social Security Numbers (SSNs), passwords, hacked email accounts and even entire identity kits. The dark web came into existence as an offshoot of government experiments with anonymous communication.
The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. The advantages of I2P are based on a much faster and more reliable network.
Protecting Yourself On The Dark Web
Users should exclusively download the Tor browser from the official torproject.org website to avoid potential security risks. Additionally, it’s recommended to disable scripts and plugins to minimize vulnerabilities. The history of the Dark Web reflects the intricate interplay between technology, privacy concerns, and the ever-evolving landscape of online activities.
Tools To Monitor Dark Web Activity
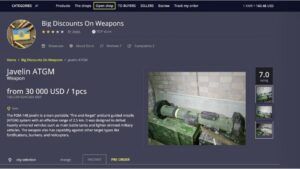
It’s possible to buy and sell illegal drugs, malware, and prohibited content in darknet marketplaces. Some dark web commerce sites have dangerous chemicals and weapons for sale. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. The subreddit r/deepweb is a good starting point for asking more experienced users about how to search the dark web and deep web for the content you want. Lastly, The Hidden Wiki is a collection of dark web links — but the links may not work and can lead to dangerous websites. The dark internet is designed to provide anonymity by keeping communication private through encryption and routing online content through multiple web servers.
These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web. This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. Darknet markets facilitate transactions for illegal goods and services. Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources.
For additional protection, enterprises should monitor the dark web to identify indicators of dark web compromise, such as database dumps or the posting of personal or financial information. Regular monitoring can provide early alerts of possible threats, which can facilitate prompt responses to mitigate the potential effects. Organizations can also consider dark web monitoring services that search through data available on the dark web for anything related to their specific company or employees. Dark web monitoring can supplement other tools used to gather preemptive threat intelligence, such as the Mitre ATT&CK framework. Indexes of website links allow Google and other search engines to return relevant results whenever a user types a keyword into the search bar.
What Is The History Of The Dark Web?
By approaching this hidden corner of the internet with informed caution and ethical awareness, you can navigate it more safely and responsibly. While no approach guarantees complete safety, a careful and skeptical mindset serves as one of your most valuable tools on the hidden internet. This article aims to shed light on the more constructive side of the dark web, guiding readers toward reputable resources and reliable information. We’ll cover the foundational principles of anonymity on networks like Tor, discuss how to navigate this hidden realm safely, and emphasize the importance of verifying sources.

Like any tool, it depends on how you use it — and how careful you are when using it. Here are 3 sites to help you browse this hidden part of the internet. Before accessing the dark web on a desktop, secure your connection with an antivirus bundled with a VPN (like Norton), then follow the steps below. Go to and download the Tor Browser Bundle, which contains all the required tools. Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser.
I Legal And Ethical Considerations
That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. As the digital world continues to evolve, the Dark Web will undoubtedly remain an important and often controversial part of the internet’s landscape. Whether used for good or ill, its shadowy nature is unlikely to fade anytime soon.