
Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. The good news is that the platform will not see what you copy/paste.
- BreachGuard will guide you through the process of recovering your accounts, helping you lock them down before a hacker can use your leaked credentials.
- The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites.
- Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
- The trick with these onion websites is their accessibility, which is made possible only with Tor.
- That allows .onion sites to be accessible anonymously without services like DNS.
How To Browse The Dark Web Legally
For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly.
Will Visiting The Dark Web Attract Attention?
Once you’re in, continue to use caution to protect your anonymity and safety. Don’t click on random links from strangers while browsing the dark web, and never give away any personal information. Remember to update the Tor Browser regularly to ensure you have the latest security patches, and scan your computer for malware regularly using antivirus software. As I mentioned above, the dark web is a decentralized, non-indexed network of web pages, and the sites don’t use standard URLs. There are marketplaces where people can sell stolen credit card numbers, conduct illegal drug transactions, and scam people out of their cash and crypto.
To access the surface web or the deep web, all you need is a standard internet browser like Google Chrome or Safari. For the dark web, though, you need an entirely different entry point known as an overlay network. Before you go much further, it’s important that you close out of other applications and software that offer malicious users on the dark web an entry point into your device or network. When closing down other applications it’s important to actually right-click and quit rather than just hitting the x in the corner of the window.
How To Uninstall The Tor Browser

In this tutorial, we’ll explain how to access the dark web in complete privacy and cover a few more important factors to consider before starting. As long as you are vigilant about your online activity, there aren’t any issues. The maximum trouble you can get into on the dark web is visiting political forums or marketplaces. In that case, the government might flag and monitor you even if you’re not a participant or trader.
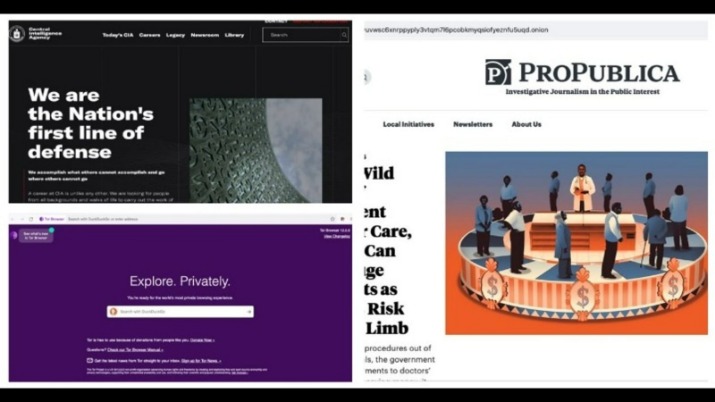
Table Of Contents
However, your online activity is encrypted and hidden from view thanks to Tor’s onion routing. This means your ISP can’t see that you’re accessing the dark web (or indeed, the specific sites you’re accessing). Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites. VPN over Tor requires you to place trust in your ISP but not your VPN and is best if you want to avoid bad Tor exit nodes. Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously). Although the official Tor Project advises against VPN over Tor, both methods are superior to not using a VPN at all.
Malicious Software

KEY TAKEAWAYS If you’re in a hurry to find out the disposable email service provider, have a q… If you choose the safest option, beware that it will disable most of the audio formats, fonts, and videos on websites and hinder the working of some websites. Moreover, the “safest” settings will cause a significantly slower internet connection. Both methods improve your online security and anonymity compared to not using a VPN.
How Do I Access Tor?
Using a VPN in conjunction with the Tor Browser is an excellent way to keep your online travels secure and private. A VPN’s ability to hide your Tor usage from your ISP and from government authorities makes for a valuable addition to your online privacy arsenal. Plus, there are only a few VPN providers that offer this option (PrivateVPN is the only one that comes to mind).
Tips On How To Access The Dark Web Safely
If you need a way to organize as an activist or you want to discuss censored topics with others, my first suggestion is to stick to offline meetups. The second, less secure option is to use encrypted messaging apps with ties to specific non-profit or activist organizations. For example, Briar is an extremely private chat app designed to help journalists communicate anonymously with sources. Signal is our Editors’ Choice for private messaging apps because it does a great job of blending privacy and social media functionality for a highly customizable chat experience. Accessing the dark web is not illegal in the United States, but naturally, engaging in illegal activity while on the dark web can get you in hot water.
It also prevents your IP address from being collected by cybercriminals on the dark web (this can happen if your traffic goes through a Tor server run by bad actors). The VPN changes your IP address, and, if you activate it before you even access Tor, you’ll be entering the network with the VPN’s IP address (this method is called Tor over VPN). However, since iOS browsers are required to use WebKit (Apple’s built-in web rendering engine), the Onion Browser doesn’t have the same level of privacy as the Tor Browser on desktop or Android.
Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. Additionally, you can opt for Subgraph OS as a second option to Tor. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. In due course, the framework was remodeled and made public as a secure browser. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
When using Tor, your traffic will never reach its intended destination directly, as it would on surface web browsers. Instead, it is funneled through different ‘nodes’ – other user’s computers – before coming out the other side. These computers are all owned by volunteers, passionate about privacy and happy to offer up their device to help others. Traffic is relayed through three nodes each time it passes through the Tor network. Using the Tor Browser is one of the best ways to protect your privacy, especially when combined with a reliable VPN. Disabling JavaScript and avoiding personal logins or revealing identifying details can further reduce the risk of being tracked.

It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. Also, you must log in or have a specific IP address or URL to access the deep web content. It works by sending internet traffic through volunteer-operated nodes all over the world.
However, Bitcoin’s relevance in the digital world has also made it a scam target. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users. Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network. The most prevalent dark web content is child pornography, about 80% of its web traffic, despite being challenging to find.



