Perhaps one of the major attraction factors of these forums is undoubtedly anonymity. Cybercriminals want to carry out their illegal activities without detection by law enforcement agencies and other authorities. The forum suffered a blow in 2018 when the creator was arrested, but despite that, Altenen has soldiered on and remains active today. FreeHacks is yet another Russian-based administrator-owned dark web community forum that offers an extensive database of hacking resources and tools. The platform focuses primarily on DDoS attacks, carding, and several other forms of cybercrime. Also known as Not Evil, this dark web search engine offers access to a wide array of .onion content.
How To Find New, Active Dark Web Links
The VPN encrypts your traffic before it enters the Tor network, preventing your ISP from seeing that you’re using Tor. This double encryption also protects against compromised Tor entry nodes that could potentially monitor your activity. While people and organizations do host legitimate and useful sites on the dark web, it’s still best to tread cautiously. Despite Tor’s privacy-focused design, malicious entities are more likely to target your data in transit and on .onion sites. Using Tor to access dark web links isn’t illegal, but your ISP will notice, and others may too.

Are Onion Sites Safe?
To appreciate why some users turn to the Hidden Wiki rather than Google, it’s important to understand the distinction between the surface web and the deep web. The surface web consists of all websites indexed by traditional search engines like Google, Bing, or Yahoo. This includes sites with publicly accessible content, such as news portals, blogs, and social media platforms. In contrast, the deep web encompasses parts of the internet not indexed by standard search engines.
Everything You Need To Know About The First Dark Web Market: The Silk Road Website
The Hidden Wiki plays a crucial role by listing verified onion links, warning users about scams, and giving descriptions to help them make informed choices. While they make accessing Tor-hidden websites easier without the Tor browser, they can compromise your privacy and security by acting as intermediaries that might expose your data. Using the Tor Browser with a VPN is a safer and more secure option, as it provides end-to-end encryption and better privacy protection. It’s simply a part of the internet that isn’t indexed by regular search engines and needs special software, like Tor, to access.
Safe Dark Web Links To Explore
- However, it also underscores its role as a gateway to an illegal and dangerous realm of the internet.
- The Dark Lair is another strong contender for those looking for dark web directories beyond the Hidden Wiki.
- The core functionality of the dark web relies on onion routing, a method that encrypts and routes user communications across multiple servers, known as nodes.
- It has a bidding feature, with new batches of stolen data being frequently added.
- Just like Facebook, this is no random namesake; it is a legitimate platform from which to reach the CIA anonymously.
- The Tor browser allows you to browse the internet anonymously and visit inaccessible sites.
They know how to process the information and get it to the correct law enforcement agencies internationally. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. The use of the dark web raises suspicion as it shows there is something you want to do privately.
Testimonials From Users
As a result, you may see adult content, gambling, or other offensive websites during your searches, so be careful about the links you click. TorLinks is a robust Dark Web directory that offers a compilation of links organized into commercial and non-commercial categories. Each category is further divided into multiple sub-categories for easy navigation. Initially launched as a backup of The Hidden Wiki, it’s now the primary go-to resource for accessing .onion sites and resources when other directories face unexpected downtimes. Both DuckDuckGo and Ahmia are safe choices for finding Tor Browser links without being tracked.
Archivetoday – Compare Sites Da Dark Web Ao Longo Do Tempo
These sites are intentionally hidden to protect the privacy and anonymity of both the site operators and visitors. The dark web consists of websites that use encrypted .onion domains, which require specific software and protocols to access. The problem is, the dark web isn’t indexed by regular search engines. Tor websites are simply websites that can only be accessed when you’re connected to the Tor network. Instead of the more familiar top-level domains (TLD), such as .com, .org, or country-specific TLDs (like .co.uk or .fr), Tor websites use the special .onion TLD.

Dark web search engines help mitigate these challenges by indexing and cataloging dark websites, making it easier for users to locate the information they need. They provide a crucial service by organizing the chaotic and often dangerous landscape of hidden websites. This article provides a current list of the top dark web search engines in 2024. Whether you’re a cybersecurity professional, researcher, or simply curious about the dark web, this article will help you navigate this hidden internet space. Using trusted directories, PGP encryption, and secure wallets helps protect against fraud. Since these markets operate in hidden networks, scams and security risks are common.
- With onion sites like Wikipedia, you can continue learning and gathering information on a wealth of issues, even in places where the standard Wikipedia is restricted or censored.
- Therefore, you must run an IP leak test to ensure that the VPN is working completely fine and is not risking your digital security.
- However, unlike commercial search engines, This is run by a confederation of volunteers.
- The dark web consists of websites that use encrypted .onion domains, which require specific software and protocols to access.
- It’s a type of collaboration that cybercriminals look for to expand their reach as well as the impact of their operations.
Tor’s official website recommends using the Orbot app for Android and the Onion Browser app for iPhone to access these websites. From timeless classics to modern works, the library provides a varied selection of reads for everyone. That said, if you’re mostly interested in open-access scientific research papers and academic articles, try Sci-Hub or Library Genesis (LibGen). ProtonMail, powered by Proton AG, provides end-to-end encryption to keep your email messages from being monitored.

The dark web is shrouded in mystery, but not every onion website is dangerous. But before we start, install Norton VPN to help protect your digital identity and stay safer online. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes.
Its interface makes it easy to identify clone websites and ensures that users always use the authentic site. Not Evil works more like a regular internet search and is the successor to TorSearch (another Tor search engine) and the Evil Wiki (another listing site). As with any Tor network search engine, you will always have mixed results. The very nature of the network means that not every address is searchable, and dark web content isn’t indexed nicely and neatly like the clearnet. Web crawlers (also known as a spider) are internet bots that systematically trawl through internet pages and index the content. An intuitive, user-friendly interface is crucial, especially given the complex nature of dark-web interactions.
Search Code, Repositories, Users, Issues, Pull Requests
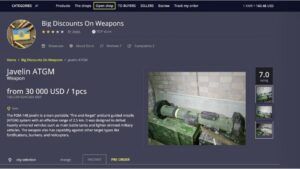
Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal information.