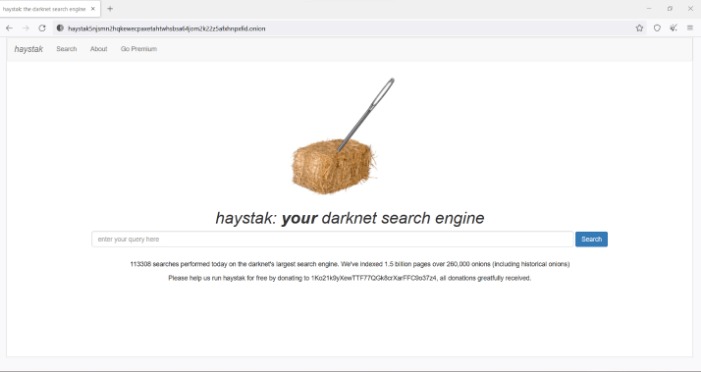
There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section.
Tor-over-VPN Vs VPN-over-Tor: The Right Order
As a general rule, never download anything at all from the dark web. There are all sorts of threats on the dark web, and it’s all but impossible to verify whether a file is legitimate, so you’re likely to inadvertently download malware to your device. Take a look at your Tor Browser settings before you start your first dark web browsing session. It has a range of settings you can configure to help with security and privacy. Disabling JavaScript, ActiveX, and Flash plugins, for example, will help to strengthen your privacy, though this may also cause some sites to run poorly. This separation helps maintain anonymity and shields genuine personal details from unauthorized access by threat actors lurking in the shadows of the clandestine online landscape.
You need a special browser to access it, and when you do, your internet traffic is not wired through the network of interrelated public servers in the way it is when you access the surface web. Also, it is worth noting that using Tor may draw attention from authorities if they suspect you are engaging in illegal activities or if your online behavior raises suspicion. Generally, it’s important to use Tor responsibly and in accordance with local laws and regulations. There is a significant risk that the government can target you for visiting a dark website, as many Tor-based sites have been taken over by police authorities worldwide. Even if a person does not make any purchases on illegal marketplaces like the Silk Road, custom software used by law officials can analyze activity and identify user identities.

Panda Security specializes in the development of endpoint security products and is part of the WatchGuard portfolio of IT security solutions. Initially focused on the development of antivirus software, the company has since expanded its line of business to advanced cyber-security services with technology for preventing cyber-crime. The landscape of the dark web (and cyberthreats in general) is constantly changing, with new threats emerging regularly.
Beginners & Casual Users
Thankfully, it allows you to connect unlimited devices, which will be useful when exploring the onion links with many devices. The VPN boasts bullet-proof 256-bit encryption, solid leak protection, a kill switch, a no-logs policy, and split tunneling to safeguard your online privacy and safety. Another feature that makes it reliable is Onion over VPN, allowing you to use the deep web anonymously. ExpressVPN is a top-notch VPN service with features like super-fast speeds on most servers, its onion site, and robust security, making it easy to browse the onion web pages. Therefore, to access the deep web, you need passwords to those databases. A regular dark web browser will only encrypt your browser traffic; Orbot goes further and encrypts all data in and out of your phone.
- If you want to improve your security further, you could also use a VPN at the same time as Tor.
- The 2024 Global Threat Report unveils an alarming rise in covert activity and a cyber threat landscape dominated by stealth.
- However, the first Tor server you connect to can see your real IP address — if a malicious actor operates it, they could collect it and use it to track your location or online behavior.
- The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives.
Navigating The Shadows: Accessing Onion Services
Let’s dive into the heart of the dark web and explore its hidden corners. While Tor enhances anonymity by masking your IP address, it is not entirely immune to tracking or surveillance. Advanced techniques or vulnerabilities could potentially compromise your anonymity, so it’s important to combine Tor with other security measures for enhanced protection. By staying vigilant and practicing safe browsing habits, you can reduce the risk of falling victim to scams, malware, or other malicious activities on the dark web. Users may encounter illegal activities, including the sale of stolen data, drugs, and weapons. Standing for The Onion Protocol, Tor is a system of network encryption designed to protect your privacy and help you stay anonymous online.
Guide To Accessing Tor Via Tails OS On A USB Thumb Drive:

Identifying specific individuals who use the dark web can be quite tricky. However, we advise connecting to one of our recommended VPN services to stay anonymous. Many dark websites are perfectly legal and safe to use and, in many cases, are better for your privacy than clear websites. When you open your default browser, Freenet will be ready and running through its web-based interface. Note you should use a separate browser than the one you normally use to help ensure anonymity. NordVPN is offering a fully-featured risk-free 30-day trial if you sign up at this page.
How To Use The Tor Browser & Stay Safe: Full Guide 2025
Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play. From choosing the right networks and privacy tools to avoiding scams and malicious software, every step you take should be guided by caution and informed judgment. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly. Below are some trustworthy starting points and authoritative references.
You can use the VPN rated #1 for the dark web with no restrictions for a month—great if you want to try this no-log provider’s Onion over VPN servers for yourself. The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode.
Keep Your Data Off The Dark Web
The Tor network operates as a free, volunteer-driven infrastructure designed to enable anonymous communication online. Onion routing, the core technique employed, involves encrypting communications in multiple layers, akin to the layers of an onion. This encrypted data is then randomly bounced through a series of relays, operated by volunteers across the globe. Each relay in this circuit decrypts only one layer of encryption, obscuring the origin and destination of the traffic from any single point of observation. This process effectively conceals users’ identities and their online activities from surveillance and traffic analysis, providing a significant degree of anonymity.
Happy Chick Software: A Complete Overview Of The All-in-One Retro Gaming Emulator
If a breach is detected, BreachGuard will notify you right away and help you take the steps you need to secure your data immediately. Dark web marketplaces offer a range of both legal and illicit goods. Here’s a look at several of the illegal items you can buy — with prices — courtesy of Privacy Affairs’s Dark Web Price Index 2023. By monitoring known dark web marketplaces, Avast BreachGuard will alert you immediately if and when your data is found.

A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor. As I mentioned previously, using the Tor Browser will slow down your browsing. Since your traffic goes through a series of relays, getting encrypted or decrypted along the way, things slow way down.
Who Created Tor?
Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Damir is the team leader, product manager, and editor at Metaverse Post, covering topics such as AI/ML, AGI, LLMs, Metaverse, and Web3-related fields.
How To Watch The Google IO 2025 Keynote
Your information might be on the dark web if it was exposed in a data breach, sold, or stolen by hackers. To check, you can use dark web scanning or breach detection tools like Avast Hack Check or LifeLock Breach Detection to search for compromised data. If found, take immediate steps to secure your accounts and personal information. The dark web can certainly be dangerous — with no regulation, it’s a riskier place to hang out than the surface web. Malware and scams are scattered like landmines around the dark web. And with many unfamiliar-looking sites on the dark web, it’s harder to distinguish safe websites from shady ones, and easier to fall victim.
Whonix uses Oracle Virtualbox to run two virtual machines (VMs) on top of your currently installed OS (Windows, Linux, or Intel-based macOS). The Whonix Gateway VM handles Tor processes, and the Whonix Workstation VM runs user applications on an isolated network. This prevents data from leaking between applications and makes your Internet traffic more secure. Your download and upload speeds may be slower, but that is the tradeoff for secure Internet browsing.



