
The Darknet is a subset of the Internet operating over encrypted, anonymous overlay networks that require special software like Tor, Freenet, or I2P. The editorial team did not participate in the creation of this guide. Gizmodo may earn a commission when you buy through links on the site. Let’s summarize the most important points from this guide on how to access the dark web. However, if you’re looking to trade or buy something, the risk of scams increases exponentially. People often make the grave mistake of divulging their private information to the seller or anyone else who can take advantage of it and harm the user in many ways.
Connect To The Tor Network
If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals. Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. Additionally, you can opt for Subgraph OS as a second option to Tor. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged.
ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions.
More On How To Stay Safe On The Dark Web
The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect. Accessing the Dark Web can expose you to a range of risks that might not be immediately apparent. While many visitors manage to browse hidden services without incident, staying safe requires constant vigilance.
VPN-over-Tor (Limits And Niche Uses)
People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. It works by sending internet traffic through volunteer-operated nodes all over the world. This network of over 6,000 relays hides your location, thus protecting you from online surveillance and third-party tracking by your websites. Identity theft monitoring is critical if you want to keep your private information from being misused. All types of personal data can be distributed online for a profit. Passwords, physical addresses, bank account numbers, and social security numbers circulate in the dark web all the time.
- Lastly, we provided a list of recommended Dark Web websites, showcasing platforms and resources dedicated to privacy, journalism, whistleblowing, and secure communication.
- Our experience has shown that this is the #1 way of doing things without risking your privacy.
- It connects you to a network of servers rather than a particular server.
- One of the darkest aspects of the dark web involves human trafficking, illegal pornography, and other forms of exploitation.
- This signifies that your internet traffic is being routed through the Tor network.
Why You Need A VPN To Be Safe On The Dark Web

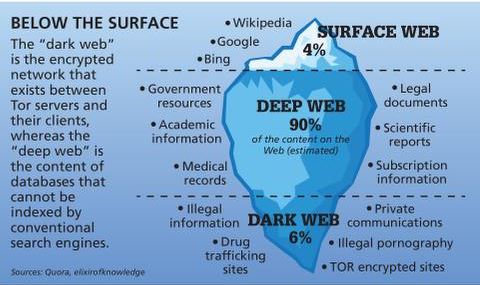
The dark web is simply a part of the internet that requires special tools like the Onion Browser to get access. Finding content on the dark web isn’t as straightforward as using Google. You’ll need a specialized dark web search engine, like Ahmia or DuckDuckGo’s Tor service, which can help you locate onion sites (also called Tor sites). This level of anonymity makes the dark web a haven for illegal activities, such as drug trafficking and various types of cybercrime. The dark web operates in a realm where privacy is paramount, but its potential for misuse requires you to tread with caution.
You may very well end up in the middle of a stakeout that could turn ugly. So, if the website looks fishy, close the tab, and forget about it. Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that).
Legal Uses Of The Dark Web
This unique browsing experience underscores the user\’s active role in navigating the intricacies of the Dark Web landscape. The dark web offers a marketplace section where users can buy legal or illegal products. These products are often bought with cryptocurrencies, and several markets thrive from this exchange to sell or buy products and services. Some popular marketplaces include AlphaBay (before it was taken down) and Hansa. Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind. Therefore, you should stay cautious and avoid clicking when accessing the dark web.
Best Dark Web Browsers Today – Detailed List
Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for. If you need to use a computer and do not want to leave evidence behind (like a digital ghost), Tails is the best tool. While it’s not a browser, it includes Tor Browser installed by default that provides anonymity for web browsing and enables users to access the dark web.
That means Javascript is disabled, extensions are disabled, and the browser is configured to warn you if an attempt is made to download a file and open it in another application. Also, since the Tor Browser is based on the Mozilla Firefox platform, it’s susceptible to the same attacks that other browsers are. While the Tor Browser and the Onion Network are an excellent way to protect your online privacy and anonymity, it is by no means a perfect solution, and it has a few weaknesses.
Using Brave Browser (with Tor)
Governments have implemented measures to trace and regulate cryptocurrency transactions. Explore the legal nuances of accessing the dark web, including potential penalties and jurisdictional differences. Proton VPN has decent connection speeds and has tools for giving long-distance connections a bump.
- Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.
- Again, it’s DOT Security’s advice to stay off the dark web entirely.
- It’s legal to access the dark web in the U.S. and most other countries.
- Suppose you share your name, social security number, or any other personally identifiable information on any dark website.
Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. That information can include checking and credit card account numbers, social security numbers, and other sensitive information. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web.
Don’t Use Your Main Device
The same general process applies to other operating systems, as Tor is also available for Mac and Linux. All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. DefCon, ProPublica, the CIA, various libraries, and open-source software providers also feature in this area of the internet. A VPN and Tor should be used together and it is advisable to connect via a VPN to Tor, rather than vice versa, for the best protection possible.



