BlackCloud offers encrypted file storage specifically optimized for the Tor network. The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations.
- At the same time, these networks can also facilitate exploitation, hate speech, and other harmful activities.
- Alternatively, if the website has turned the onion URL into a link, you can click on that in the Tor browser, and it will automatically open the dark website.
- For this reason, you cannot browse through these sites using your default search engine.
- Your traffic is relayed and encrypted three times as it passes over the Tor network.
Wide Area Network (WAN): Definition, Examples, And Technologies
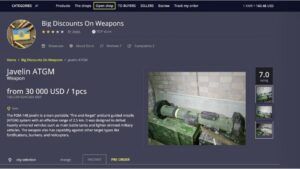
It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. Others are looking for stolen data, hacking services, or even banned books and political content.
How Can I Access The Dark Web Safely?
KEY TAKEAWAYS If you live in a country where you don’t have internet freedom and face extreme … Moreover, you can use a Tor circuit, but it won’t improve security; instead, it will surely improve the browsing speed. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice. Darknet Proxy, an uncomplicated Tor proxy site, offers access to the dark web without requiring installation.
How To Install The Tor Browser On Android
Sometimes, you can access a website but won’t be able to login on your Tor browser. Likewise, some websites allow Tor, but with frequent Captchas that can be annoying. Tor is slower than standard browsers because it routes your traffic through multiple servers.
SRWare Iron, another Chromium-based browser ardently focused on privacy, eliminates Google tracking services and UI modifications. Epic Browser, staunchly committed to privacy, integrates built-in proxy support. It facilitates access to select dark web content through global proxy servers. This article aims to give a thorough analysis of the top ten darknet browsers for 2023, rating them according to privacy, security, and usability standards. We’ll go into great detail about the benefits and drawbacks of each browser, supported by a useful comparison table.
Darknet Proxy
Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic. Hence, it’s advisable not to download files via Tor, especially from unknown sources. The last node (exit node), through which Tor routes your traffic, is delicate. In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts. Whenever you enter any domain into the address bar, your browser uses HTTP to find and request the data from the relevant server.

Customize Your Browsing Experience
Furthermore, deanonymization may be possible as a result of browser flaws. The Tor browser stands as the venerable luminary of darknet browsers, leveraging onion routing and encryption for unparalleled anonymity. Developed under the aegis of the non-profit Tor project, with sponsorship from the U.S. government and various organizations. The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results.
A Dark Web Search Engine
Registration is easy and the site is accessible via both the dark web and clear web. Newly registered users cannot view any of this market’s listings though until they deposit at least $50 of Litecoin, Bitcoin, or Ethereum. The emergence of Telegram as a new dark web frontier also partly explains the revenue reductions in traditional dark web marketplaces. That way, you can change your passwords and protect your accounts before anyone can use your data against you.
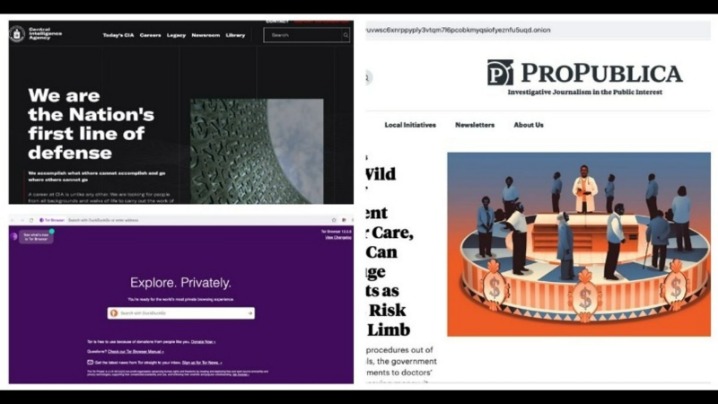
Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy.

To safeguard yourself against phishing, fraud, and other threats, it’s crucial to verify the authenticity of links before engaging with any dark web platform. These are the top 10 dark web search engines that allow easier access to the hidden corners of the internet. These search engines allow users to access onion dark web pages without setting up expermental labs or using specialized equipments. It was quite popular for selling a wide range of products and services.
Other Built-in Tor Features You Should Know
You can use the Tor or Onion browser to access the Dark Web on Android and iOS devices. If you exercise due caution and use a combination of the Tor browser and common sense in which sites you access on the dark web, yes, the dark web is safe to use. You may be targeted by law enforcement, exploited by hackers, or threatened by criminals using the dark web for nefarious purposes. By using Tor over VPN, the VPN encrypts your data and hides your IP address.
Keep Your Identity Hidden
While the Tor network provides a level of security, vulnerabilities can still expose you to cyber threats. To minimize these risks, it’s crucial to follow best practices for security while accessing the Dark Web, including the use of VPNs. Many sites on the Dark Web engage in illegal activities, such as drug trafficking and financial fraud.