Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. Additionally, hidden wiki websites function as directories of categorized .onion links, providing common entry points for users delving into the hidden internet. These search engines catalog .onion domains, which are not easily accessible from regular web browsers. These top 10 dark web search engines are important for research, evidence collection, finding hidden resources, intelligence, and various other resources that are not easily accessible.
Best Laptops For Cybersecurity Students In 2025 The U

Now that there are organizations that employ trained and certified cybersecurity experts to detect vulnerabilities and gaps, hackers have other motivations. The evolution of these motivations really goes hand-in-hand with the evolution of hacking, in general. Hackers have evolved over time, which has made defending cybercrime a challenging task.
Future-Proofing Your Business: Cybersecurity Predictions For 2025

ProPublica’s Tor version is a beacon for investigative journalism in the digital age. Explore the dark web threats facing healthcare today, their potential risks, and effective responses. A technology strategy framework is essential for businesses to effectively leverage technology to enhance operational efficiency, customer experience, and foster innovation while managing risks. This framework is often referred to as IT strategy or digital strategy. By adopting these strategies, businesses and individuals can better protect themselves against the ever-evolving threats of the dark web.
ProtonMail — Anonymous And Encrypted Email Service
However, while browsing the dark web itself is lawful, taking part in illegal activities — like buying or selling illegal goods or engaging in criminal behavior — is not. To stay on the right side of the law, be cautious about what you access and ensure you follow the rules in your region. Before you embark on your journey into the Dark Web, it’s crucial to establish a secure foundation. While the Tor network is designed to provide anonymity, it alone cannot guarantee your privacy or safety. This section will guide you through the essential preparatory steps and tools to ensure that you remain as protected as possible while exploring hidden services and tor onion domains.
Regulations on the use of cryptocurrency on the dark web links could have both short-term and long-term effects on the market. In the short term, it could lead to a decrease in demand for cryptocurrency on the dark web websites as buyers and sellers adjust to the new regulations. However, in the long term, it is possible that the market could adapt to the new regulations, and continue to thrive.
Securing Virtualized Environments – Hypervisor Security Best Practices
This added layer of security keeps your identity hidden and shields you from online threats. The “Dark Web” often conjures up images of hidden marketplaces, illicit trades, and shadowy figures lurking in the digital underworld. The Dark Web is simply a part of the internet that cannot be reached by standard search engines and browsers. Cryptocurrency regulations can have a significant ripple effect on various types of dark net markets. Darknet markets are online marketplaces that are accessible through dark web links and typically offer illegal goods and services such as drugs, weapons, and stolen data. Cryptocurrencies are often the preferred method of payment on these platforms due to their anonymity and lack of regulation.
Which Is The Best Laptop For Cyber Security Course?

Another critical advantage of the Hidden Wiki lies in its resistance to censorship. This makes it an essential resource for users living under oppressive regimes or in countries with strict internet controls. The Hidden Wiki empowers people to access alternative viewpoints, engage in uncensored discussions, and exercise freedom of information that surface web search engines cannot guarantee. Torch is one of the more established dark web search engines, designed to help users navigate the Tor network and discover onion sites. Unlike traditional search engines like Google or DuckDuckGo, Torch indexes hidden websites that operate beyond the reach of the surface web.
Although profiting from pirated copyrighted material is unethical and illegal, there are some exceptions to using copyrighted material, such as a “private study” provision under UK law. The CIA is contactable on the dark web, providing a completely anonymous way to get in touch with them. However, if you’re communicating with state intelligence agencies, you should use Tor alongside a VPN for maximum privacy.
To access them, copy and paste the hyperlinks provided into the Tor browser. In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends. While these marketplaces continue to serve legitimate purposes, such as enabling secure communication and privacy protection, they also remain hotspots for illicit activities and cybercrime.
Encrypted Messaging Apps And Private Communities
- It relies on P2P connections and requires specialized tools and software.
- TorLinks serves as a backup or secondary directory site to the popular Hidden Wiki.
- Archive.today is considered an important tool to track changes across government and corporate websites, preserve cultural heritage, and keep knowledge outside of autocrats’ reach.
- It also conducts searches across both the clearnet and dark web by leveraging multiple indices, so you can filter searches to focus exclusively on the darknet or span both realms.
Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user.
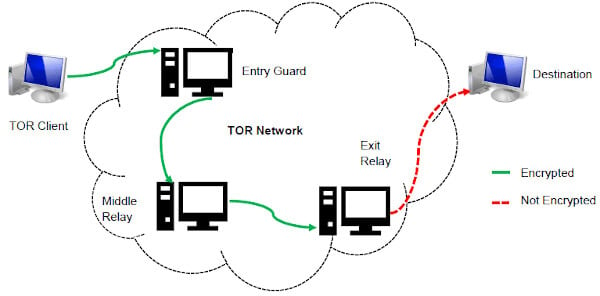
It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web. Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. The only difference is that it passes your traffic through random nodes before reaching the destination.
These platforms are harder to track and often rely on decentralized reputation systems. You can also use it for hosting websites which will use your computer as the host server. That said, if ProtonMail doesn’t suit your needs, there are other Dark Web email platforms available, such as RiseUp and Mail2Tor. For example, RiseUp is an invite-only platform, meaning that you will need an invitation to use it. Stay safe and informed as you explore the deeper layers of the internet. Some do, like Ahmia; others like Torch index nearly everything, including illicit content.
Can Search Engines Find Everything On The Dark Web?
Instead of browsing indexed links, dark web engines scour encrypted, often anonymous websites (“.onion” sites) that do not exist on the clear or surface web. Since regular search engines don’t index .onion sites, finding what you need on the dark web can be tricky. That’s where dark web search engines come in — they help you discover hidden websites and make navigating this part of the internet easier. In this guide, you’ll find the top 9 dark web search engines, complete with .onion links. Each one offers unique features, such as better privacy and extensive .onion site indexing.

Some of these people are no less than heroes who in some cases put their security on the line to share information that could be beneficial to the rest of the world. The information they share can be quite risky which is why using a platform like ProPublica can be the best thing for them. ProPublica is one of the most popular legitimate sites on the dark net. It takes advantage of the privacy and anonymity offered by the dark net. This is why activists and journalistic sources usually share sensitive information with investigative journalists through this platform. It is also a popular platform for whistleblowers as it offers a great level of anonymity.
Is It Illegal To Access The Dark Web?
The cybersecurity challenges seen in 2024 highlight the dynamic and ever-evolving nature of cyber threats. As cryptors, loaders, and stealers become more sophisticated, and underground markets remain resilient, organizations must prioritize robust cybersecurity measures in 2025. This shift will likely drive forum operators to introduce features like automated escrow services and enhanced anonymity to attract users. Black traffic schemes—malicious landing pages promoted via deceptive ads—remained a constant threat. These schemes leveraged mainstream ad platforms to distribute malware to unsuspecting users.